KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Ransomware attacks extended into the industrial sector last year to such a degree that this type of incident became the number one threat in the industrial sector.
Two ransomware groups, LockBit and Conti, have been most active compromising organizations with an Industrial Control System (ICS)/Operational Technology (OT) environment in 2021.
A report today from industrial cybersecurity company Dragos highlights that the industrial sector has become a more attractive target for both financially motivated adversaries and actors linked to state-sponsored groups.
Also Read: The Competency Framework: A Guide for Managers and Staff
Monitoring the threat activity in the industrial sector last year, the company discovered a jump in ransomware incidents targeting ICS/OT networks.
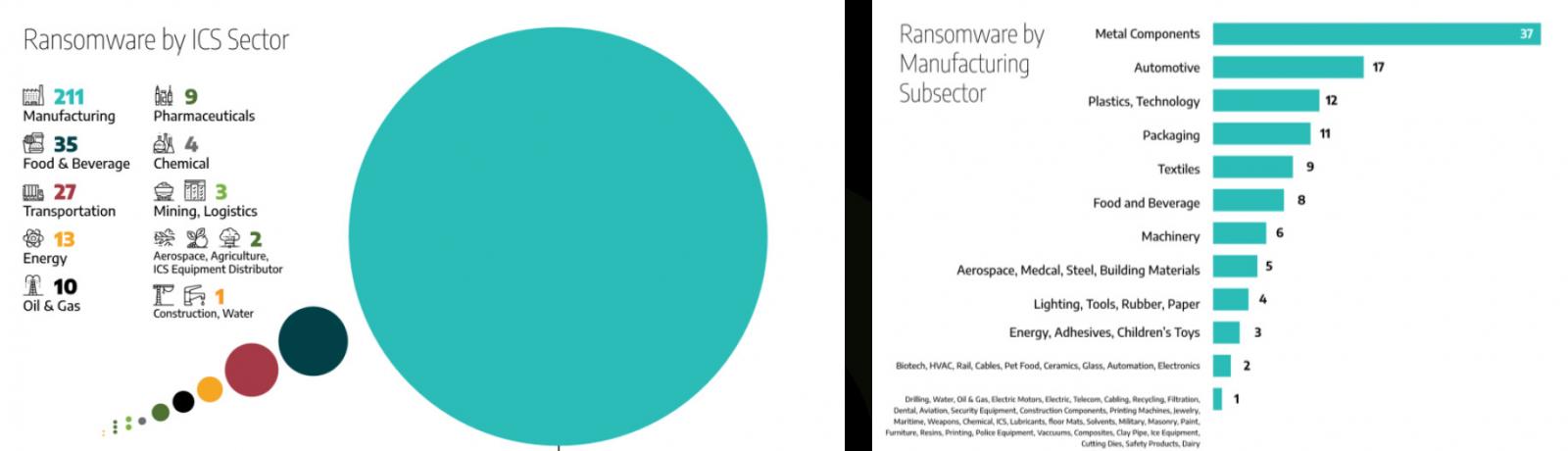
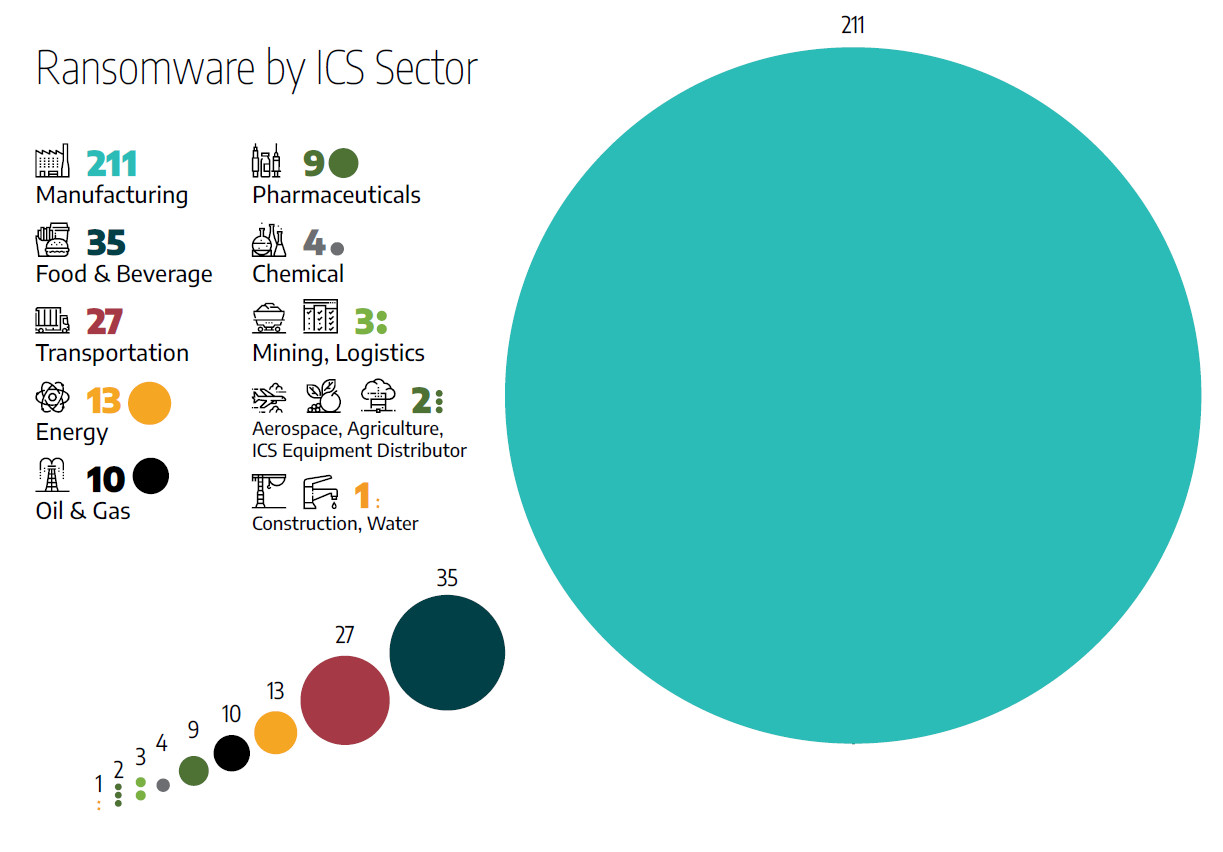
According to Dragos’ findings, the most common targets for ransomware groups were in the manufacturing sector, with 211 attacks accounting for 65%, followed by 35 successful compromises of companies in the food and beverages business, and 27 attacks against entities in the Transportation sector.
The researchers note that the manufacturing vertical is the most exposed to attacks because this “sector is often the least mature in their OT security defenses.”
An overview of the security of these companies reveals a troubling trend, the researchers say based on data collected during customer engagements
Many organizations have very limited visibility into the infrastructure, fail to properly segment network perimeters, have many devices with an external connection, and a large percentage of shared credentials between the enterprise network (IT) and the OT environment
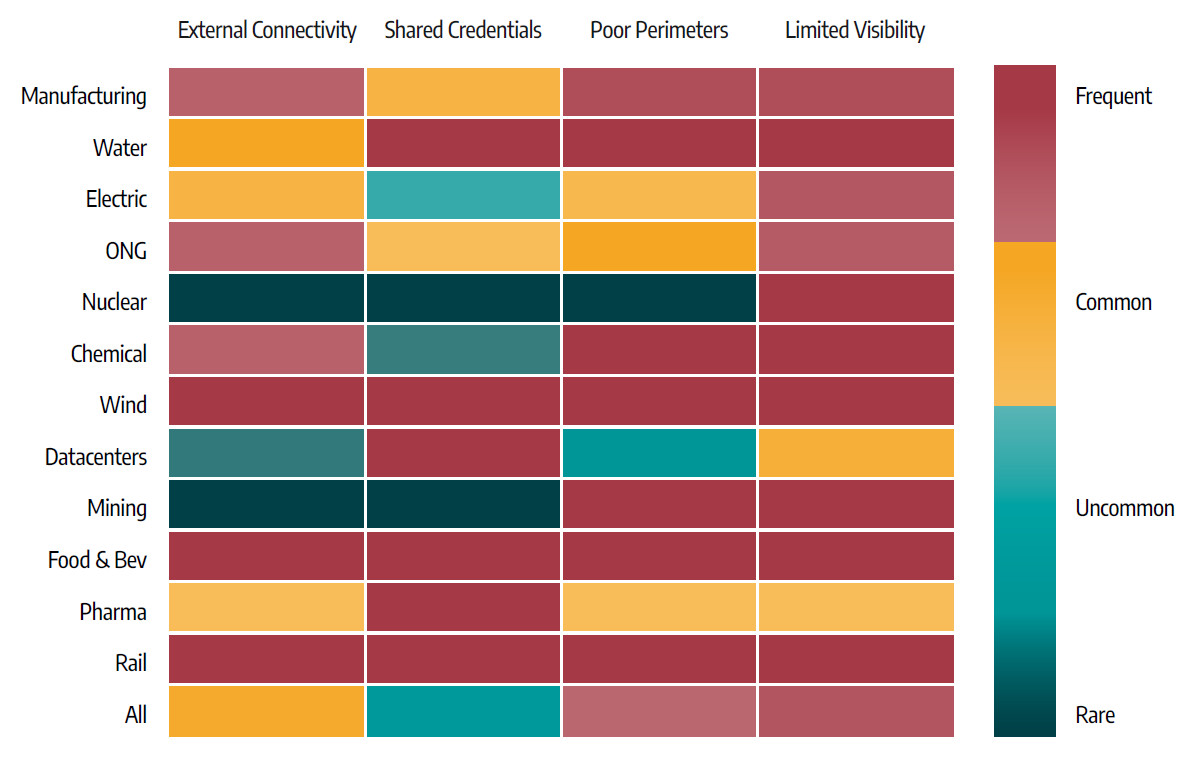
The problems above lay the ground for successful attacks, allowing threat actors to pivot from the IT network into the OT segment, even if breaching the latter is not the main goal.
Also Read: Personal Data Protection Act Australia
This allowed the ransomware threat to become the number one cause for compromises in the industrial sector, the researchers note in the report.
“While ransomware mainly targets enterprise IT systems, there are a number of instances when it does impact OT directly and in integrated IT and OT environments” – Dragos
After gaining access to the IT network to execute the ransomware component, adversaries can move laterally into OT systems, allowing them to ask for larger ransoms by causing a more damaging impact.
Of the ransomware groups attacking the industrial infrastructure, LockBit and Conti are by far the most active, accounting for 51% of the incidents.
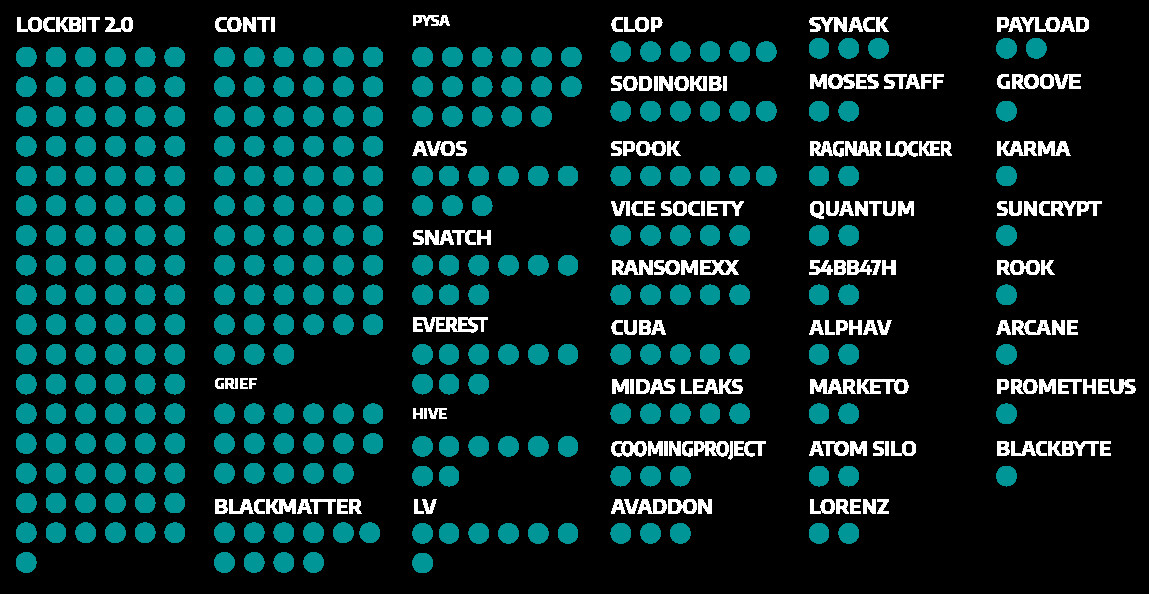
According to Dragos, the two ransomware groups are responsible for 166 attacks on companies in the ICS sector, LockBit accounting for 103 incidents and Conti for 63. The latter has taken control of the TrickBot operation recently and will likely increase its incursions into OT networks.
In 70% of all the ransomware incidents that Dragos analyzed, the targets were in the manufacturing sector, the most affected subsectors being metal products, automotive, plastics, technology, and packaging.
Ransomware threats are not showing any decline, despite governments prioritizing law enforcement efforts to bring ransomware-as-a-service (RaaS) operators and their affiliates to justice.
Dragos has high confidence that this threat will keep disrupting industrial operations and OT environments in 2022 because of either of the following three factors: