KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The infamous Maze ransomware gang announced today that they have officially closed down their ransomware operation and will no longer be leaking new companies’ data on their site.
Last week, BleepingComputer reported that Maze had stopped encrypting new victims since the middle of September, cleaned up their data leak site, and was extorting their final victims.
Today, Maze released a press release titled “The Project is closed,” where they state that they are closed and any other ransomware operation that uses its name is a scam.
“Maze Team Project is announcing it is officially closed. All the links to out project, using of our brand, our work methods should be considered to be a scam.
We never had partners or official successors. Our specialists do not works with any other software. Nobody and never will be able to host new partners at our news website. The Maze cartel was never exists and is not existing now. It can be found only inside the heads of the journalists who wrote about it.”
BleepingComputer has asked Maze if they would be willing to release the master decryption keys when they close their support site like was done with Crysis, TeslaCrypt, and Shade. We have not received a response to this question.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
Maze Ransomware rose to prominence in November 2019, when they stole unencrypted files and then publicly released them after a victim did not pay. Soon after, other ransomware operations began copying this double-extortion strategy, which has now become commonplace for almost all ransomware operations.
Maze is known for attacking well-known and large organizations such as Southwire, City of Pensacola, Canon, LG Electronics, and Xerox.
Threat actors have told BleepingComputer that some of the Maze affiliates have moved to a new ransomware operation called Egregor, who recently attacked Crytek, Ubisoft, and Barnes and Noble.
Egregor, Maze, and another ransomware called Sekhmet, are believed to be created from the same software.
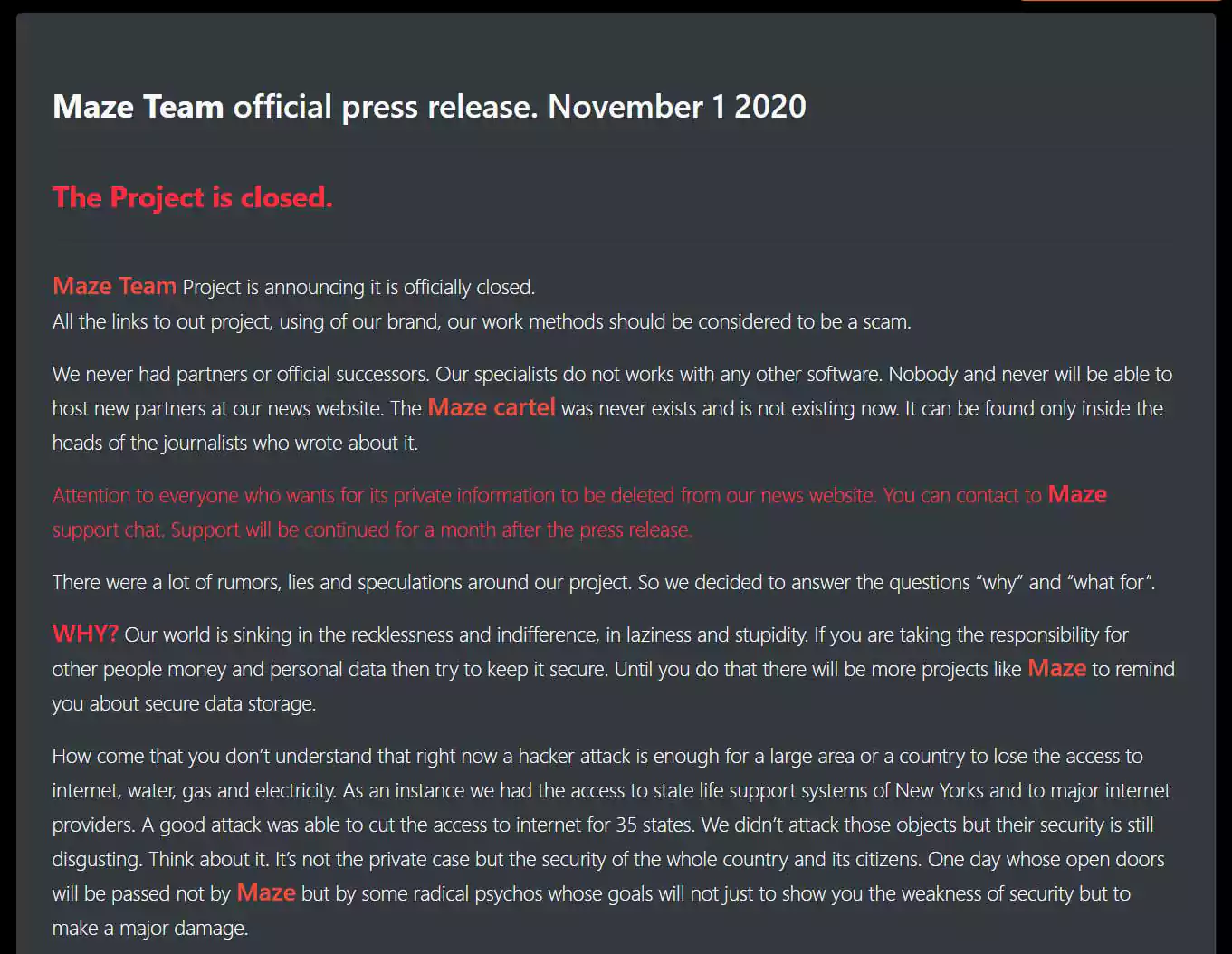
In June 2020, it was noticed that the Maze group had added information about a victim from a different ransomware operation called LockBit.
To learn more about this collaboration between Maze and LockBit, BleepingComputer contacted the ransomware operators and was told that they are now collaborating with other groups to share information and experiences.
“In a few days another group will emerge on our news website, we all see in this cooperation the way leading to mutual beneficial outcome, for both actor groups and companies.”
“Even more, they use not only our platform to post the data of companies, but also our experience and reputation, building the beneficial and solid future. We treat other groups as our partners, not as our competitors. Organizational questions is behind every successful business,” Maze told BleepingComputer.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
After learning of this, BleepingComputer called their new collaboration a ‘Ransomware Cartel,’ which the Maze operators quickly adopted as shown by a screenshot of data leaked on the ‘Maze News Site.’
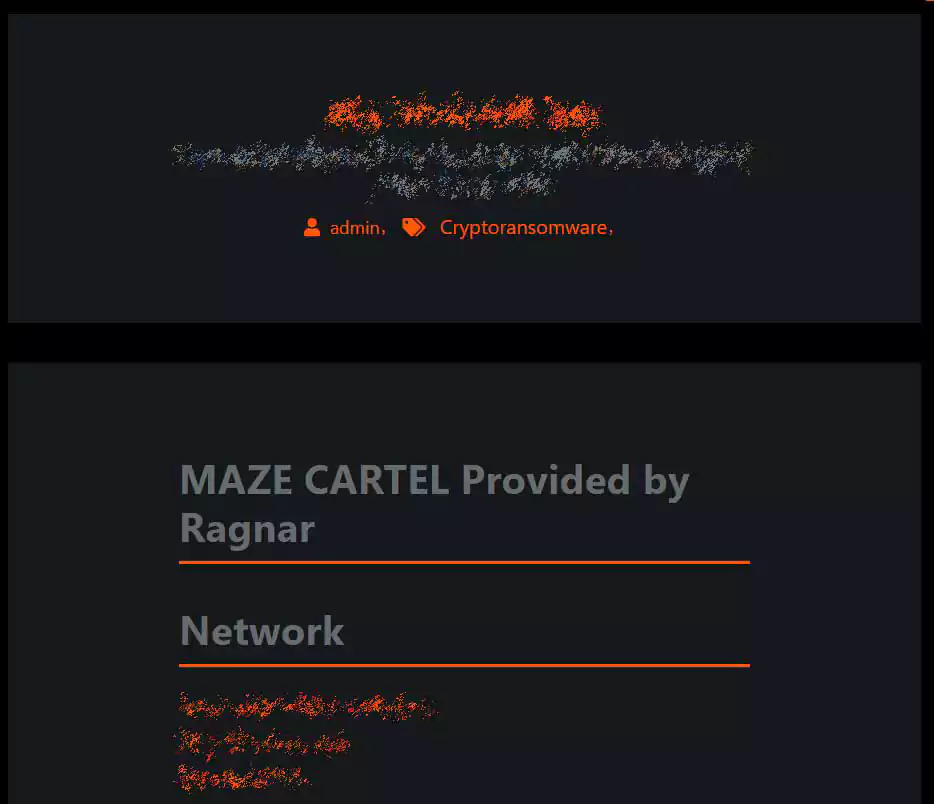
In today’s post, Maze states that this is all a fabrication, and that ‘Maze Cartel only existed inside the heads of journalists who wrote about it.’
To what extent this “Maze Cartel” existed and the collaboration between its members is unknown.