KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A ransomware targeting an Israeli company has led researchers to track a portion of a ransom payment to a website promoting sensual massages.
The attack was conducted by a more recent ransomware operation known as Ever101 who compromised an Israeli computer farm and proceeded to encrypt its devices.
In a new report by Israeli cybersecurity firms Profero and Security Joes, who performed incident response on the attack, the Ever101 is believed to be a variant of the Everbe or Paymen45 ransomware.
When encrypting files, the ransomware will append the .ever101 extension and drop a ransom note named !=READMY=!.txt in each folder on the computer.
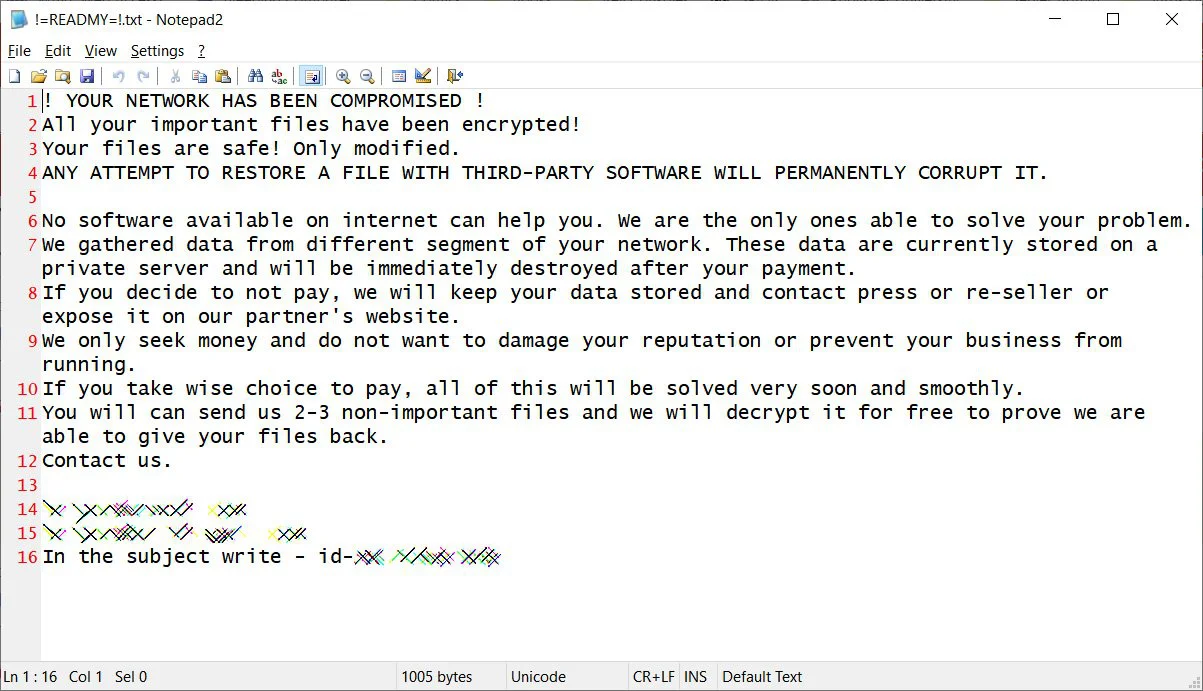
While investigating one of the infected machines, the researchers found a ‘Music’ folder that contained various tools used during the attack, providing insight into the threat actor’s tactics, techniques, and procedures.
Also Read: Compliance Course Singapore: Spotlight on the 3 Offerings
“During our investigation of the infected machines, we came across what seemed to be a treasure trove of information stored in the Music folder. It consisted of the ransomware binary itself, along with several other files—some encrypted, some not—that we believe the threat actors used to gather intelligence and propagate through the network,” explains Profero’s and Security Joe’s report.
The known tools used by the Ever101 gang include:
Other tools were also found but were encrypted by the ransomware. Based on the names and other characteristics, the researchers believe the ransomware gang used the following tools as well:
Of interest is that some of the files shared by the attackers, such as WinRar, were localized in Arabic.
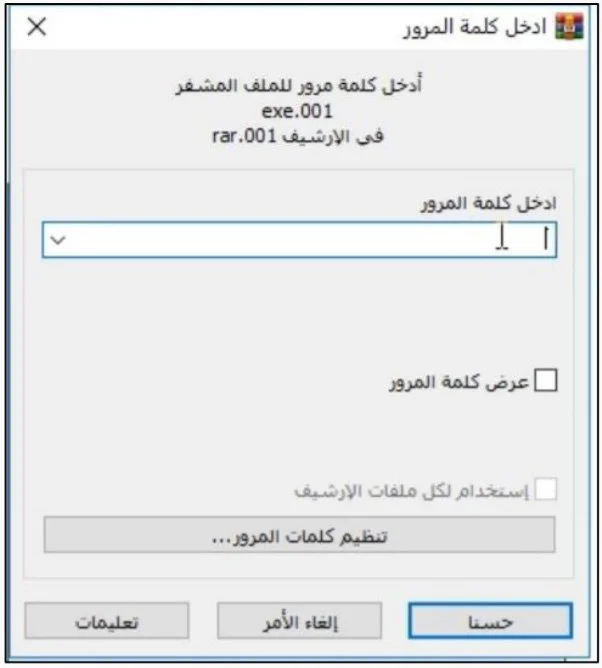
Profero CEO Omri Moyal told BleepingComputer that he believes the Arabic localization to some of these tools is a “false flag.”
Of particular interest is what the researchers discovered after they used CipherTrace to track the ransom payment as it flowed through different bitcoin wallets.
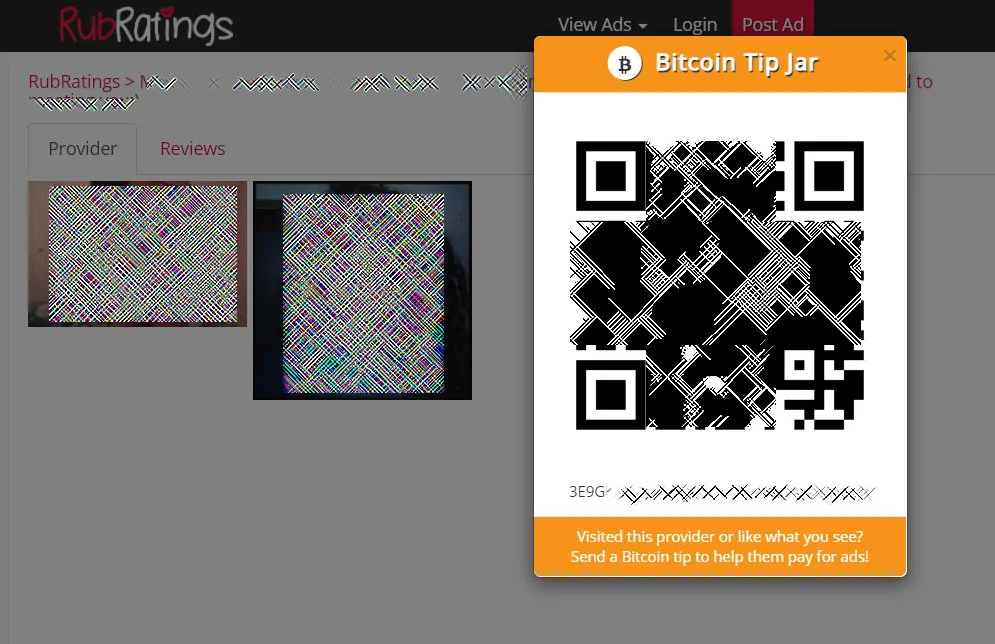
While tracing the payment, they found a small portion, 0.01378880 BTC or approximately $590, was sent to a ‘Tip Jar’ on the RubRatings site.
RubRatings is a website that allows “massage and body rub providers” in the USA to advertise their services, many of them offering sensual massages and showing barely nude pictures.
Each masseuse profile includes a Tip Jar button that allows customers to leave a bitcoin tip for their recent massage.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
The researchers believe that some of the ransom payment went to an Ever101 operative in the USA, who then used the coins to tip a masseuse, or more likely, use the site as a way to launder the ransom payment.
“The second possibility is that the provider on the site was used as another method of obfuscating the bitcoin movement,” the researchers explain. “It could be that the provider who possesses the bitcoin wallet in question was working with the threat actor(s), but more likely, it is a fake account set up to enable money transfers.”
“The bitcoin in the wallet linked to RubRatings received the payment around 15:48 UTC, and it left the wallet just a few minutes later, at 15:51 UTC.”
As bitcoin is becoming more easily traced, and even recovered by law enforcement, ransomware operations are looking for novel approaches to launder their ill-gotten gains.
It is likely that the threat actors created a fake account on RubRatings and were using the Tip Jar feature as a way to launder the ransom by making it look like a tip to a masseuse.