KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Image: Jon Hunter
New Android malware can root infected devices to take complete control and silently tweak system settings, as well as evade detection using code abstraction and anti-emulation checks.
The malware, dubbed AbstractEmu by security researchers at the Lookout Threat Labs who found it, was bundled with 19 utility apps distributed via Google Play and third-party app stores (including the Amazon Appstore, the Samsung Galaxy Store, Aptoide, and APKPure).
Also Read: 5 Workplace Tips: Protecting Information on Mobile Devices
Apps bundling the malware included password managers and tools like data savers and app launchers, all of them providing the functionality they promised to avoid raising suspicions.
The malicious apps were removed from the Google Play Store after Lookout reported their discovery. However, the other app stores are likely still distributing them.
Lite Launcher, an app launcher and one of the apps used to deliver the AbstractEmu malware on unsuspecting Android users’ devices, had over 10,000 downloads when taken down from Google Play.
“AbstractEmu does not have any sophisticated zero-click remote exploit functionality used in advanced APT-style threats, it is activated simply by the user having opened the app,” the Lookout researchers said.
“As the malware is disguised as functional apps, most users will likely interact with them shortly after downloading.”
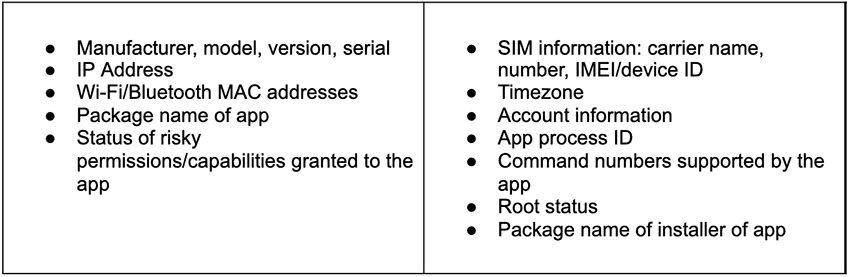
Once installed, AbstractEmu will begin harvesting and sending system information to its command-and-control (C2) server while the malware waits for further commands.
To root Android devices it infects, AbstractEmu has multiple tools at its disposal in the form of exploits targeting several vulnerabilities, including CVE-2020-0041, a bug never exploited in the wild by Android apps before this.
The malware also uses a CVE-2020-0069 exploit to abuse a vulnerability found in MediaTek chips used by dozens of smartphone manufacturers that have collectively sold millions of devices.
The threat actors behind AbstractEmu also have enough skills and tech know-how to add support for more targets to publicly available code for CVE-2019-2215 and CVE-2020-0041 exploits.
“This is a significant discovery because widely-distributed malware with root capabilities have become rare over the past five years,” the Lookout researchers said.
Also Read: The Role of A DPO During Work From Home
“By using the rooting process to gain privileged access to the Android operating system, the threat actor can silently grant themselves dangerous permissions or install additional malware — steps that would normally require user interaction.”
AbstractEmu will wait for commands from its C2 server, which can instruct it to harvest and exfiltrate files based on how new they are or match a given pattern, root infected devices, or install new apps
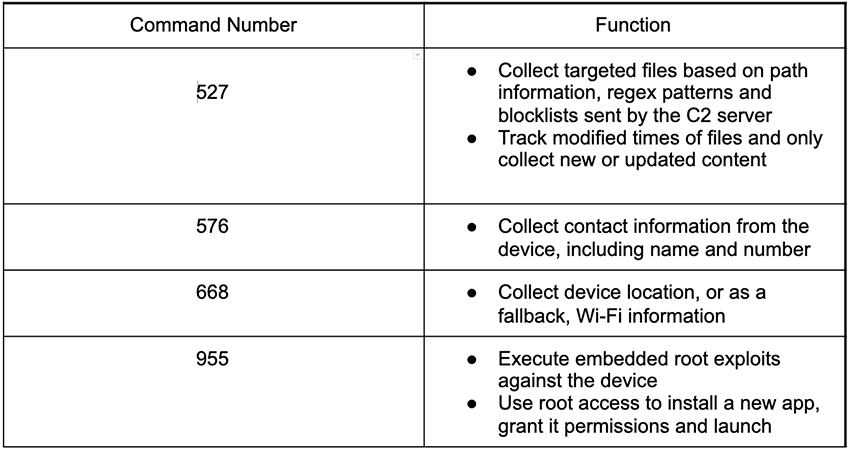
Additional actions AbstractEmu can perform after rooting an infected device range from monitoring notifications, capturing screenshots, and recording the screen to locking the device and even resetting the device password.
“Elevated privileges also give the malware access to other apps’ sensitive data, something not possible under normal circumstances,” the researchers added.
Indicator of compromise and additional technical information, including anti-emulation and device inspection techniques, can be found in the Lookout report.