KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






A new backdoor has been targeting supercomputers across the world, often stealing the credentials for secure network connections by using a trojanized version of the OpenSSH software.
The malware is not widespread and appears to target mostly high-performance computers (HPC) and servers on academic and research networks.
Security researchers at cybersecurity company ESET discovered the malware and named it Kobalos, after the misbehaving creature in Greek mythology.
They say that Kobalos has a small but complex codebase that can execute on other UNIX platforms (FreeBSD, Solaris). Some artifacts discovered during the analysis indicate that there may also be variants for AIX and Windows operating systems.
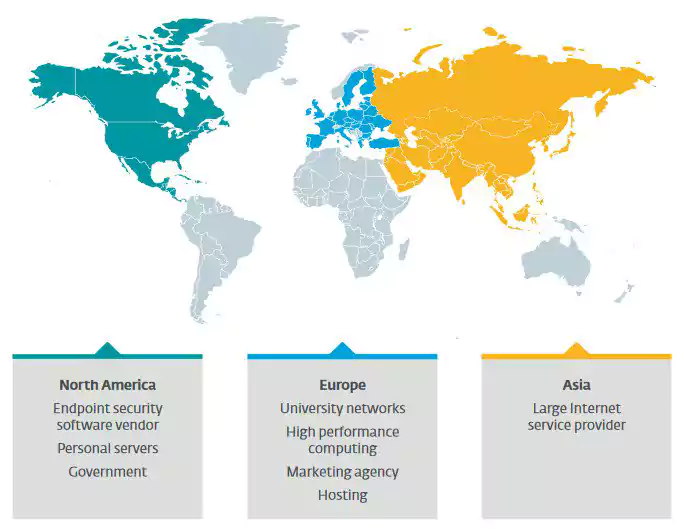
After creating a fingerprint for the threat, ESET ran internet-wide scans to find Kobalos victims. They discovered that many of the compromised systems were supercomputers and servers in the academic and research sector. Other victims include an endpoint of an undisclosed software security vendor in North America, a large ISP in Asia, marketing agencies, and hosting providers.
Also Read: Letter of Consent MOM: Getting the Details Right
ESET could not establish the initial attack vector that allowed the hackers to gain administrative access to install Kobalos. However, some of the compromised systems “ran old, unsupported, or unpatched operating systems and software,” so exploiting a known vulnerability is a likely scenario.
Although the researchers spent months analyzing the malware, they could not determine its exact purpose because of the generic commands included and no specific payload.
Kobalos provides remote access to the file system and it can spawn terminal sessions, which lets the attackers run arbitrary commands. Some details are available, though.
“On compromised machines whose system administrators were able to investigate further, we discovered that an SSH credential stealer was present in the form of a trojanized OpenSSH client. The /usr/bin/sshfile was replaced with a modified executable that recorded username, password and target hostname, and wrote them to an encrypted file” – ESET
The researchers believe that credential theft could explain how the malware spreads to other systems on the same network or other networks in the academic sector since students and researchers from multiple universities may have SSH access to supercomputer clusters.
Despite being lightweight, only 24KB for 32/64-bit samples, Kobalos is a complex piece of malware with custom obfuscation and anti-forensics techniques that hinder its analysis, and with plenty of features for its small size.
An interesting feature that sets Kobalos apart is that its code is bundled into a single function and there is only one call from the legitimate OpenSSH code to it. It has a non-linear control flow, though, recursively calling that function to perform subtasks – supports a total of 37 actions, one of which can turn any compromised machine into a command and control (C2) server for others.
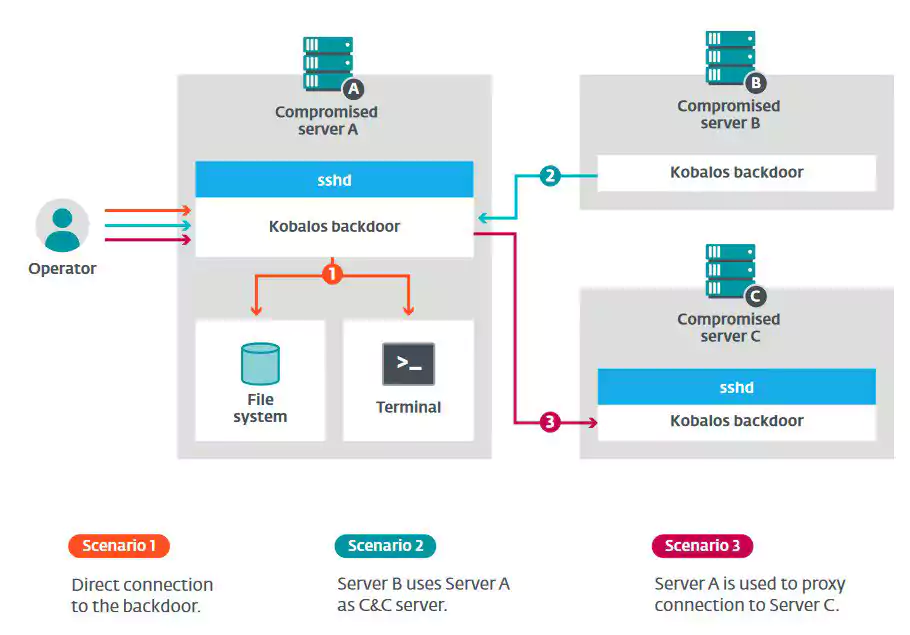
The researchers discovered that remote operators have three options to connect to Kobalos:
Kobalos also encrypts the traffic to and from the attackers. To achieve this, clients need to authenticate using an RSA-512 key and a password. The key generates and encrypts two 16-byte keys that encrypt the communication using the RC4 stream cipher.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
Furthermore, the backdoor can switch communication to an alternative port and act as a proxy (chainable) to reach other compromised servers.
Given the tiny codebase and the power it packs, ESET says that the sophistication of Kobalos “is only rarely seen in Linux malware,” which indicates a developer with much better skills than the average Linux malware author.
While the complexity of the malware is undisputed, questions remain about the attacker’s objective and the period Kobalos has been in use (some of the strings found relate to Windows 3.11 and Windows 95, which are more than 25 years old).
What is certain is that Kobalos is stealing SSH credentials from high-profile victims that include high-performance computer clusters and that it has been active before other attacks against supercomputers recorded since late 2019.
Furthermore, unlike the already reported incidents involving HPC networks, system administrators did not find any attempt to mine for cryptocurrency or run computationally expensive tasks in the case of Kobalos.
ESET notified all Kobalos victims they could identify and worked with them to remediate the infection. The researchers published a full technical analysis of Kobalos that includes indicators of compromise (IoCs) that can help potential victims detect the malware.