KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An ongoing spyware campaign dubbed ‘PhoneSpy’ targets South Korean users via a range of lifestyle apps that nest in the device and silently exfiltrate data.
The campaign deploys a powerful Android malware capable of stealing sensitive information from the users and taking over the device’s microphone and camera.
Also Read: What a Vulnerability Assessment Shows and How It Can Save You Money
Researchers at Zimperium who discovered the campaign reported their findings to the US and South Korean authorities, but the host that supports the C2 server is yet to be taken down.
The ‘PhoneSpy’ spyware comes disguised as a Yoga companion app, the Kakao Talk messaging app, an image gallery browser, a photo editing tool, and more.
Zimperium identified 23 laced apps that appear as harmless lifestyle apps, but in the background, the apps run all the time, silently spying on the user.
To do that, the apps ask the victim to grant numerous permissions upon installation, which is the only stage where cautious users would notice signs of trouble.
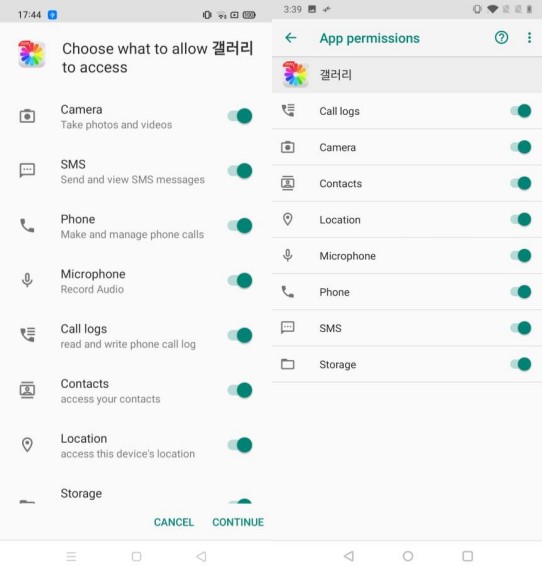
The spyware that is hiding inside the masqueraded apps can do the following on a compromised device:
The spectrum of the stolen data is wide enough to support almost any malicious activity, from spying on spouses and employees to conducting corporate cyber-espionage and blackmailing people.
Also Read: What You Need to Know About Singapore’s Data Sharing Arrangements
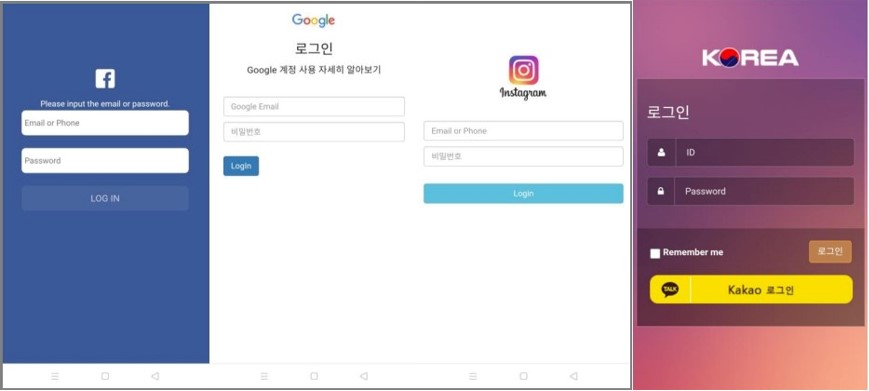
Apart from the spyware functionality, some apps also actively try to steal people’s credentials by displaying fake login pages for various sites.
Phishing templates used in the PhoneSpy campaign mimick Facebook, Instagram, Kakao, and Google account login portals.
The initial distribution channel for the laced apps is unknown, and the threat actors did not upload the apps to the Google Play Store.
It could be distributed through websites, obscure party APK stores, social media, forums, or even webhards and torrents.
A potential distribution method may be via SMS sent by the compromised device to its contact list since the malware is capable.
Using SMS texts increases the chances of the recipients tapping on the link that leads to downloading the laced apps as it comes from a person they know and trust.

If you think you might have downloaded a risky app carrying spyware, delete it immediately and then run an AV scanner to clean your device of any remnants.
In cases where privacy and security are imperative, perform a factory reset on the device.