KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new ransomware operation named Rook has appeared recently on the cyber-crime space, declaring a desperate need to make “a lot of money” by breaching corporate networks and encrypting devices.
Although the introductory statements on their data leak portal were marginally funny, the first victim announcements on the site have made it clear that Rook is not playing games.
Also Read: Compliance Course Singapore: Spotlight on the 3 Offerings
.jpg)
Researchers at SentinelLabs have taken a deep dive into the new strain, revealing its technical details, infection chain, and how it overlaps with the Babuk ransomware.
The Rook ransomware payload is usually delivered via Cobalt Strike, with phishing emails and shady torrent downloads being reported as the initial infection vector.
The payloads are packed with UPX or other crypters to help evade detection. When executed, the ransomware attempts to terminate processes related to security tools or anything that could interrupt the encryption.
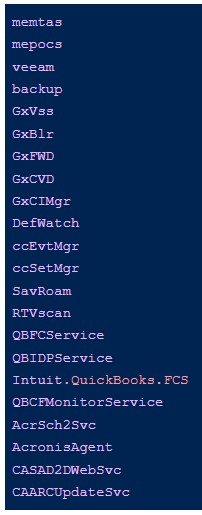
“Interestingly, we see the kph.sys driver from Process Hacker come into play in process termination in some cases but not others,” SentinelLabs explains in its report.
“This likely reflects the attacker’s need to leverage the driver to disable certain local security solutions on specific engagements.”
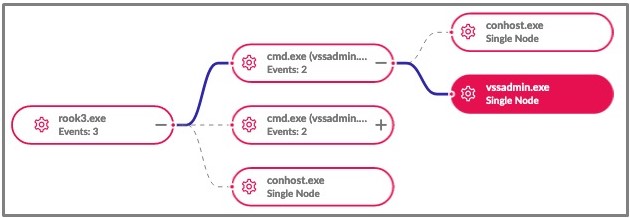
Rook also uses vssadmin.exe to delete volume shadow copies, a standard tactic used by ransomware operations to prevent shadow volumes from being used to recover files.
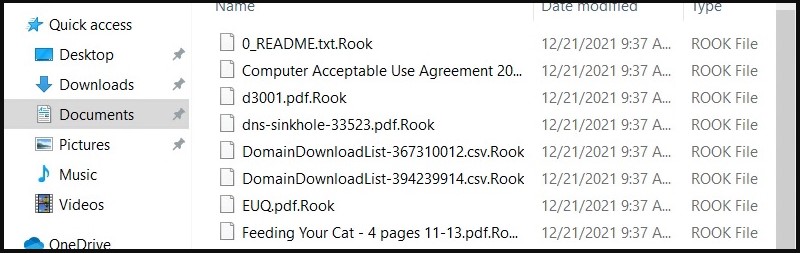
Analysts have found no persistence mechanisms, so Rook will encrypt the files, append the “.Rook” extension and then delete itself from the compromised system.
Also Read: Considering Enterprise Risk Management Certification Singapore? Here Are 7 Best Outcomes
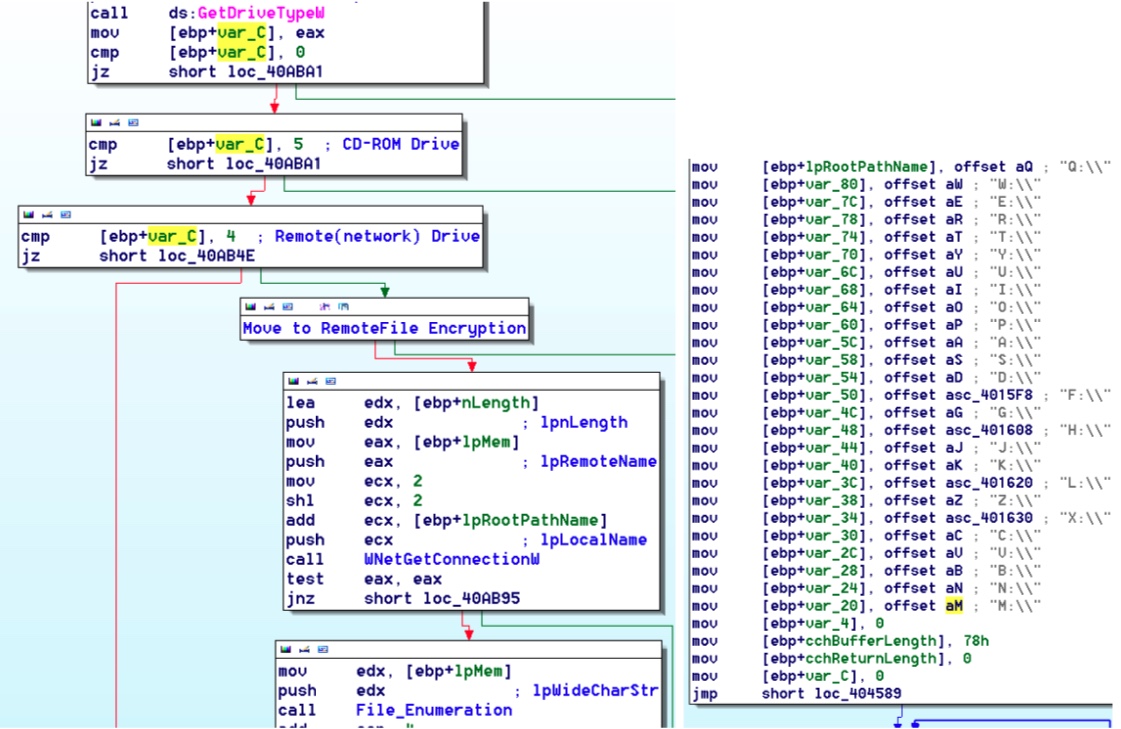
SentinelLabs has found numerous code similarities between Rook and Babuk, a defunct RaaS that had its complete source code leaked on a Russian-speaking forum in September 2021.
For example, Rook uses the same API calls to retrieve the name and status of each running service and the same functions to terminate them.
Also, the list of processes and Windows services that are stopped are the same for both ransomware.
This includes the Steam gaming platform, the Microsoft Office and Outlook email client, and Mozilla Firefox and Thunderbird.
Other similarities include how the encryptor deletes shadow volume copies, uses the Windows Restart Manager API, and enumerates local drives.
Due to these code similarities, Sentinel One believes that Rook is based on the leaked source code for the Babuk Ransomware operation.
While it is too soon to tell how sophisticated Rook’s attacks are, the consequences of an infection are still severe, leading to encrypted and stolen data.
The Rook data leak site currently contains two victims, a bank and an Indian aviation and aerospace specialist.
Both were added this month, so we are at an early stage in the group’s activities.
If skilled affiliates join the new RaaS, Rook could become a significant threat in the future.