KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Delta Electronics, a Taiwanese electronics company and a provider for Apple, Tesla, HP, and Dell, disclosed that it was the victim of a cyberattack discovered on Friday morning.
Delta claims to be the world’s largest provider of switching power supplies and reported sales of over $9 billion last year.
In a statement shared on January 22, 2022, the company said the incident impacted only non-critical systems, which had no significant impact on its operations. AdvIntel “Andariel” platform detected the attack on January 18.
Delta is now working on restoring systems taken down during the attack and says it hired the services of third-party security experts to help with the investigation and recovery process.
Also Read: Deemed Consent PDPA: How Do Businesses Comply?
The electronics provider also said it notified government law enforcement agencies to assist with the follow-up investigation.
While Delta’s statement did not say who was behind the attack, an undisclosed information security company found a Conti ransomware sample deployed on the company’s network, as CTWANT first reported.
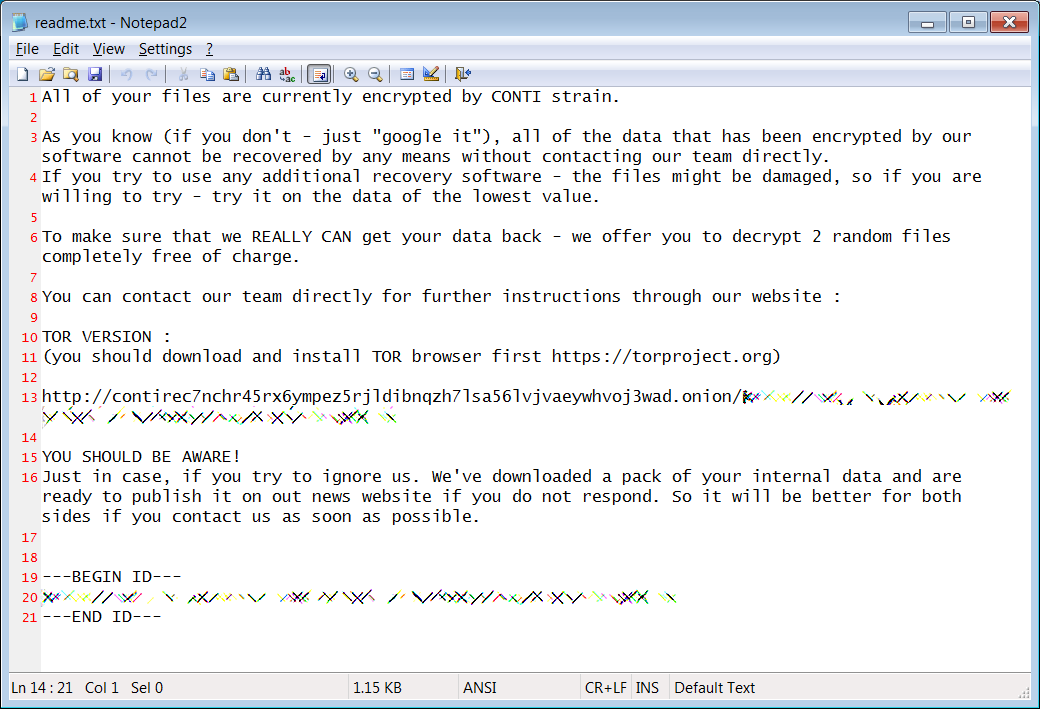
According to negotiations between Conti and Delta (also seen by BleepingComputer), the Conti operators claim to have encrypted 1,500 servers and 12,000 computers out of roughly 65,000 devices on Delta’s network.
The Conti ransomware gang asked Delta to pay a $15 million ransom for a decryptor and stop leaking files stolen from its network. Also promised a discount if the company would pay quickly.
While Delta is still reportedly working with Trend and Microsoft’s security teams to investigate the incident and claims that its production has not been affected, its website is still down one week after the attack.
Also Read: 6 Types Of Document Shredder Machine Singapore Services
Delta’s customers can use this alternate domain while the company brings back online its main website, still down following the ransomware attack, as The Record found.
“The Conti ransomware group revealed a specific pattern part of the Delta attack leveraging Cobalt Strike with Atera for persistence as revealed by our platform adversarial visibility. Certainly, this attack is reminiscent of the REvil Quanta one affecting one of the Apple suppliers,” Vitali Kremez, CEO of AdvIntel, told BleepingComputer.
Conti is a Ransomware-as-a-Service (RaaS) operation linked to the Russian-speaking Wizard Spider cybercrime group.
The ransomware gang’s operators have breached other high-profile orgs in the past, including Ireland’s Department of Health (DoH) and Health Service Executive (HSE), and the RR Donnelly (RRD) marketing giant.
A Delta Electronics spokesperson was not available for comment when contacted by BleepingComputer earlier today.