KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






This week we have seen a concerted attack against the healthcare industry by hacking groups utilizing the Ryuk ransomware. Also, we saw some large well-known companies suffer ransomware attacks that impacted their business operations.
The biggest news this week is the U.S. government warning the healthcare industry that there is “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” As a result of these attacks, we have seen six hospitals targeted in attacks this week, including Wyckoff Hospital, University of Vermont Health Systems, Sky Lakes Medical Center, and St. Lawrence Health System.
We also learned of ransomware attacks against well-known companies, such as furniture manufacturer SteelCase, French IT consulting firm Sopra Steria, and the Italian power company Enel Group.
Finally, an REvil representative known as UNKN stated that they earned $100 million in a year, and the infamous Maze gang has started to shut down its ransomware operation.
Now that the weekend is upon us, it is important for all companies to monitor for suspicious activity on their networks and Windows domain controllers, and proactively respond if anything is detected.
Contributors and those who provided new ransomware information and stories this week include: @PolarToffee, @VK_Intel, @struppigel, @BleepinComputer, @malwrhunterteam, @malwareforme, @demonslay335, @jorntvdw, @Seifreed, @FourOctets, @serghei, @LawrenceAbrams, @Ionut_Ilascu, @DanielGallagher, @fwosar, @MarceloRivero, @Malwarebytes, @Amigo_A_, @GrujaRS, @0x4143, @fbgwls245, @siri_urz, @Mandiant, and @IntelAdvanced.
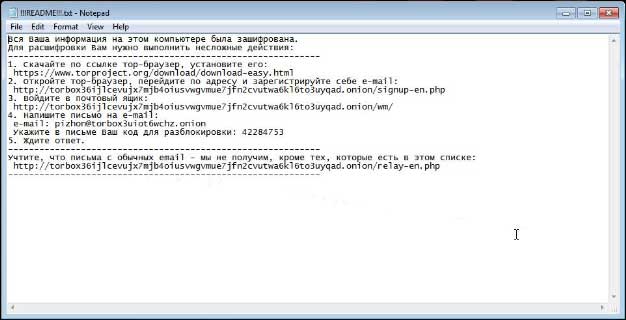
dnwls0719 found a new ransomware targeting Russia that appends the .pizhon-(Random) extension to encrypted files.
In late September, Coveware’s CEO, Bill Siegel, was invited to testify before the Federal Spending Oversight Subcommittee of the Committee on Homeland Security and Governmental Affairs. The topic: Defending Our State & Local Communities from Cyber Threats Amid COVID-19. The committee hearing was postponed after the passing of Ruth Bader Ginsberg, and while we look forward to the hearing be rescheduled, we figured would publish our submitted testimony anyway. The testimony explains the market dynamics of ransomware, and our thoughts on how to most efficiently and effectively protect our state & local communities from cyber threats.
French enterprise IT services company Sopra Steria confirmed today that they were hit with a Ryuk ransomware attack on October 20th, 2020.
Michael Gillespie found a new STOP ransomware variant that appends the .iiss extension to encrypted files.
Michael Gillespie found a new Xorist ransomware variant that appends the .ZaLtOnextension to encrypted files.
Also Read: Thinking of Shredding or Burning Paper? Here’s What You Should Know
Minerals Technologies Inc. (the “Company”) today announced that on October 22, 2020, it detected a ransomware attack impacting certain of its information technology systems. Immediately upon its detection of the security incident, which prevented access to certain systems and data within the Company’s network, the company implemented its cyber security emergency response plan. As part of that plan, Company took steps to restore its network and resume normal operations as quickly as possible. The Company launched an investigation working with industry-leading cybersecurity firms, engaged legal counsel, notified law enforcement and is in the process of notifying appropriate governmental authorities.
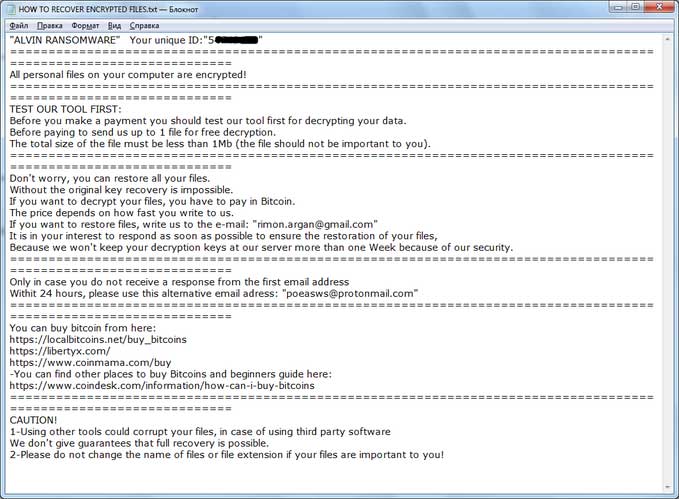
Amigo-A found a new variant of TheDMR Ransomware that calls itself ‘Alvin Ransomware’ and appends the .ALVIN extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.txt.
Karsten Hahn found ransomware written in Rust called Ransomware32 that appends the ._encrypted extension and drops a ransom note named README_encrypted.txt.
Networks of giant energy company Enel have been hit by a ransomware attack for the second time this year. This time, it’s Netwalker asking $14 million ransom for the decryption key.
Office furniture giant Steelcase has suffered a ransomware attack that forced them to shut down their network to contain the attack’s spread.
Michael Gillespie found a new ransomware that appends the .mars extension to encrypted files and drops a ransom note named !!!MARS_DECRYPT.TXT.
MalwareHunterTeam found ‘Ransomware COVID’ that appends the .crypt extension to encrypted files.

0x4143 found a new ransomware called SnapDragon that appends the .SNPDRGN extension to encrypted files.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
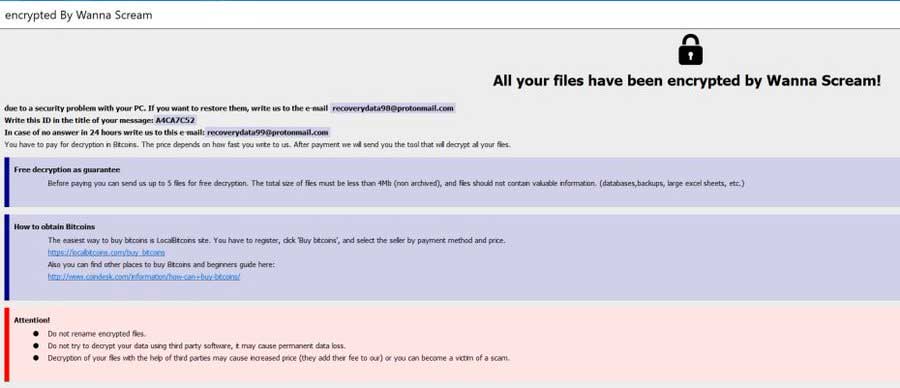
0x4143 found a new Wanna Scream variant that appends the .H@RM@ extension and drops ransom notes named info.hta and ReadMe.txt.
In recent weeks, we’ve observed a number of phishing attacks against universities worldwide which we attributed to the Silent Librarian APT group. On October 19, we identified a new phishing document targeting staff at the University of British Columbia (UBC) with a fake COVID-19 survey.
GrujaRS found a new Ragnar Locker ransomware variant that appends the .__r4gN4r__XXXXXXX extension and drops a ransom note named !!!_READ_ME_XXXXXXX_!!!.txt.
MalwareHunterTeam found the RegretLocker ransomware that appends the .mouse extension and drops a ransom note named HOW TO RESTORE FILES.TXT.
The Maze cybercrime gang is shutting down its operations after rising to become one of the most prominent players performing ransomware attacks.
REvil ransomware developers say that they made more than $100 million in one year of extorting large businesses across the world from various sectors.
In a joint statement, the U.S. government is warning the healthcare industry that a hacking group is actively targeting hospitals and healthcare providers in Ryuk ransomware attacks.
Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network are the latest victims of the Ryuk ransomware attack spree covering the healthcare industry across the U.S.
The DoppelPaymer ransomware gang has released unencrypted data stolen from Hall County, Georgia, during a cyberattack earlier this month.
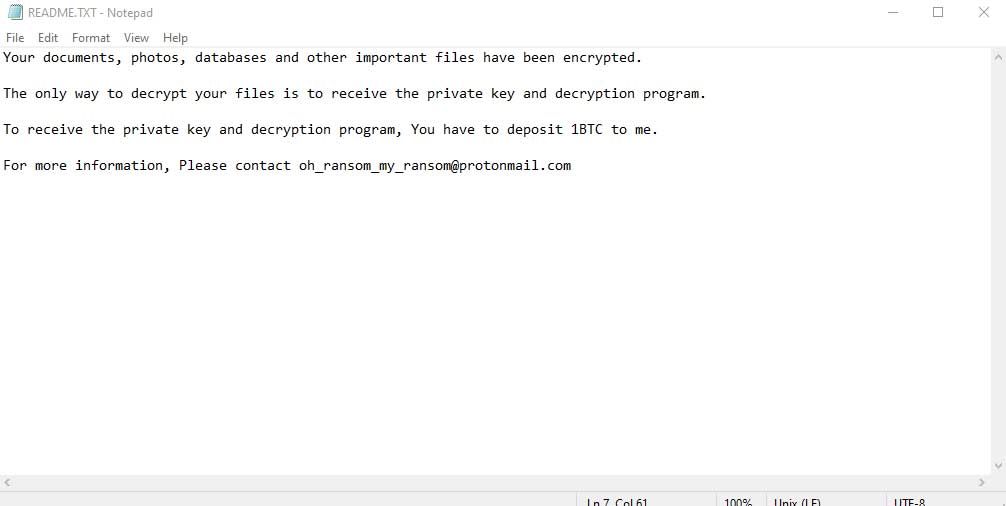
GrujaRS found a new ransomware called MyRansom that does not append an extension but drops a ransom note named README.TXT.
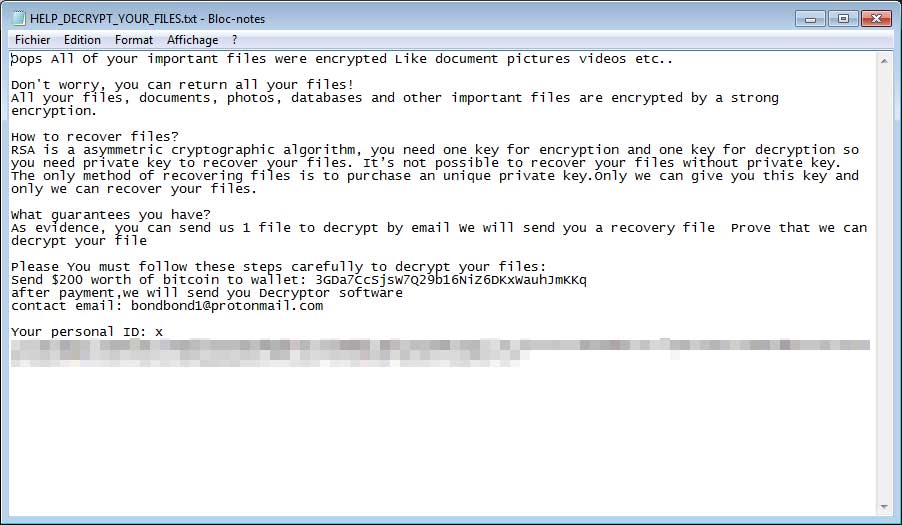
Siri found the Bondy Ransomware that appends the .bondy extension and drops a ransom note named HELP_DECRYPT_YOUR_FILES.txt.
Michael Gillespie found a new STOP ransomware variant that appends the .jdyi extension to encrypted files.
Michael Gillespie found a new Wanna Scream variant that appends the .Bang extension to encrypted files.
Siri found a variant of the CCE ransomware that appends the .aieou extension to encrypted files.
0x4143 found a new in-development ransomware called Ransomkart that appends the .ransomkart extension.
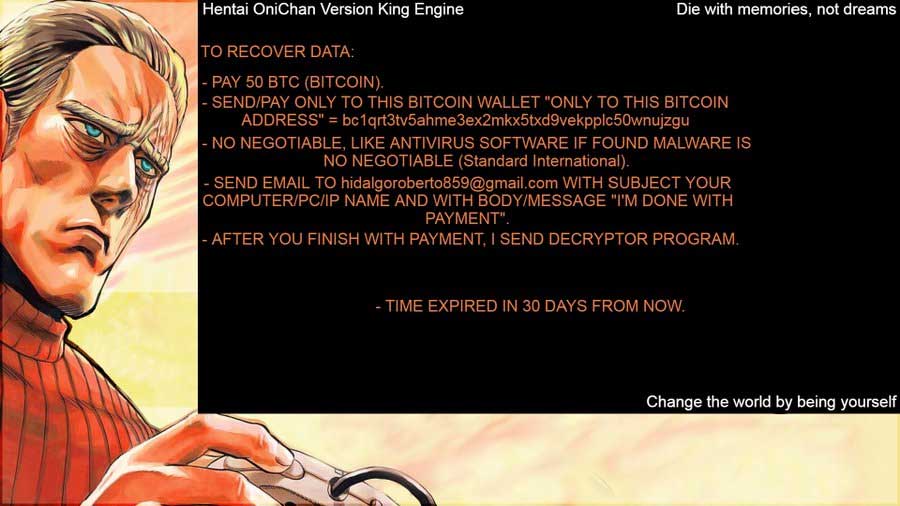
Siri found a new ransomware that calls itself ‘Hentai OniChan Version King Engine’ and appends the .docm extension to encrypted files.
Siri found another Bondy Ransomware variant that appends the .Connect extension.
Universal Health Services (UHS), a Fortune 500 hospital and healthcare services provider, says that it has managed to restore systems after a September Ryuk ransomware attack.