KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Scanning service VirusTotal announced today a new feature called Collections that lets researchers create and share reports with indicators of compromise observed in security incidents.
Indicators of compromise (IoCs) are pieces of data (files, digital addresses) uncovered when investigating cyberattacks, which can help researchers and companies detect an attack in early stages or defend against them.
VirusTotal Collections gives researchers an easy way to store, update, and share IoCs with other members of the infosec community, building more context around security incidents and threat actors.
Also Read: 7 Simple Tips On How To Create A Good Business Card Data
“Collections are open to our VirusTotal Community (registered users) and they will be enhanced with VirusTotal analysis metadata providing the latest information we have for the IoCs, along with some aggregated tags” – Juan Infantes, software engineer at VirusTotal
Threat researchers can use collections to add separate IoC groups (file hashes, IP addresses, URLs, domains) into one report that comes with a title and an op description.
All IoCs in a collection are accompanied by data from the VirusTotal, which includes the detection rate, first and last time the artifact was seen, and file size.
With domains names and IP addresses, the service also provides the name of the registrar, country, and the autonomous system, and the managing network operator, just like in the case of individual searches of security incident artifacts.
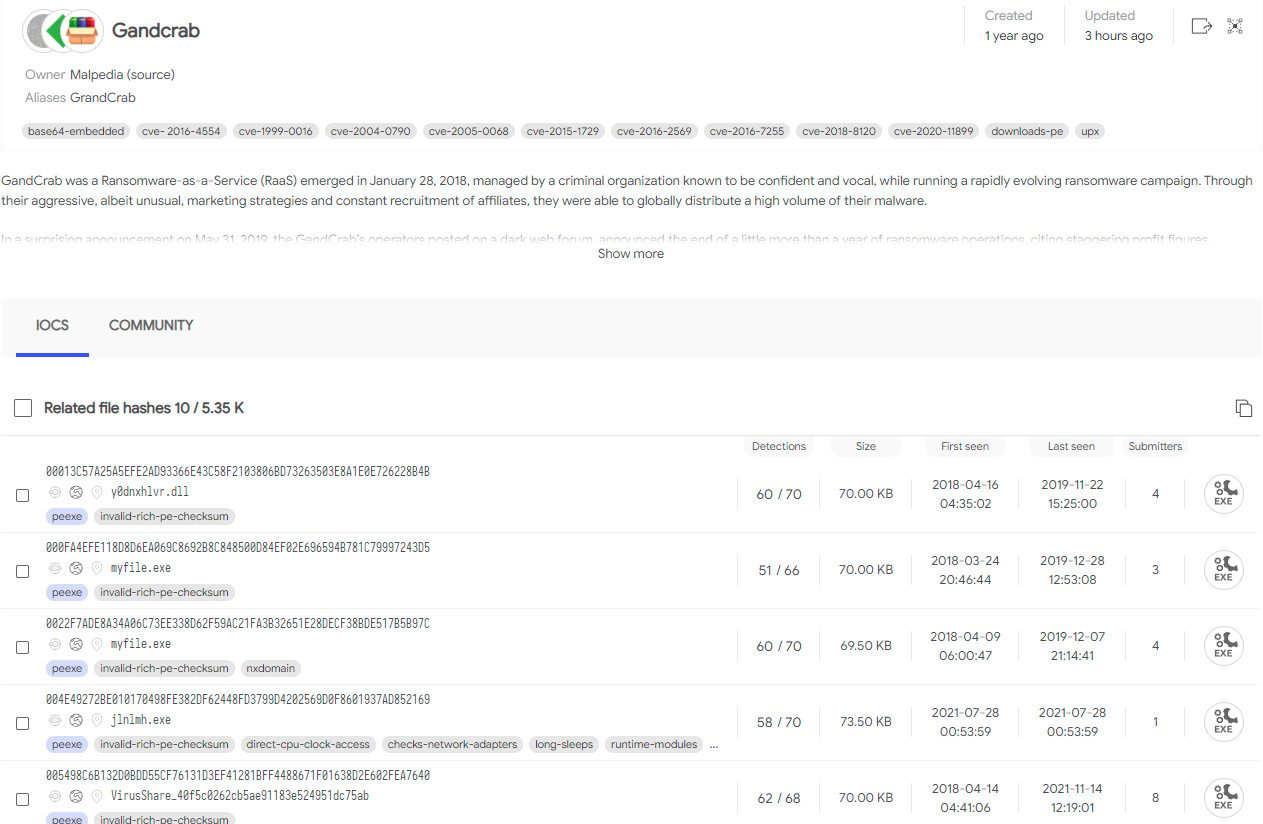
Below is an example of the collection of indicators of compromise for the defunct GandCrab ransomware, from Malpedia free resource for malware investigators.
Malpedia’s GandCrab IoC collection of file hashes:
Also Read: Trusted Data Sharing Framework IMDA Announced In Singapore
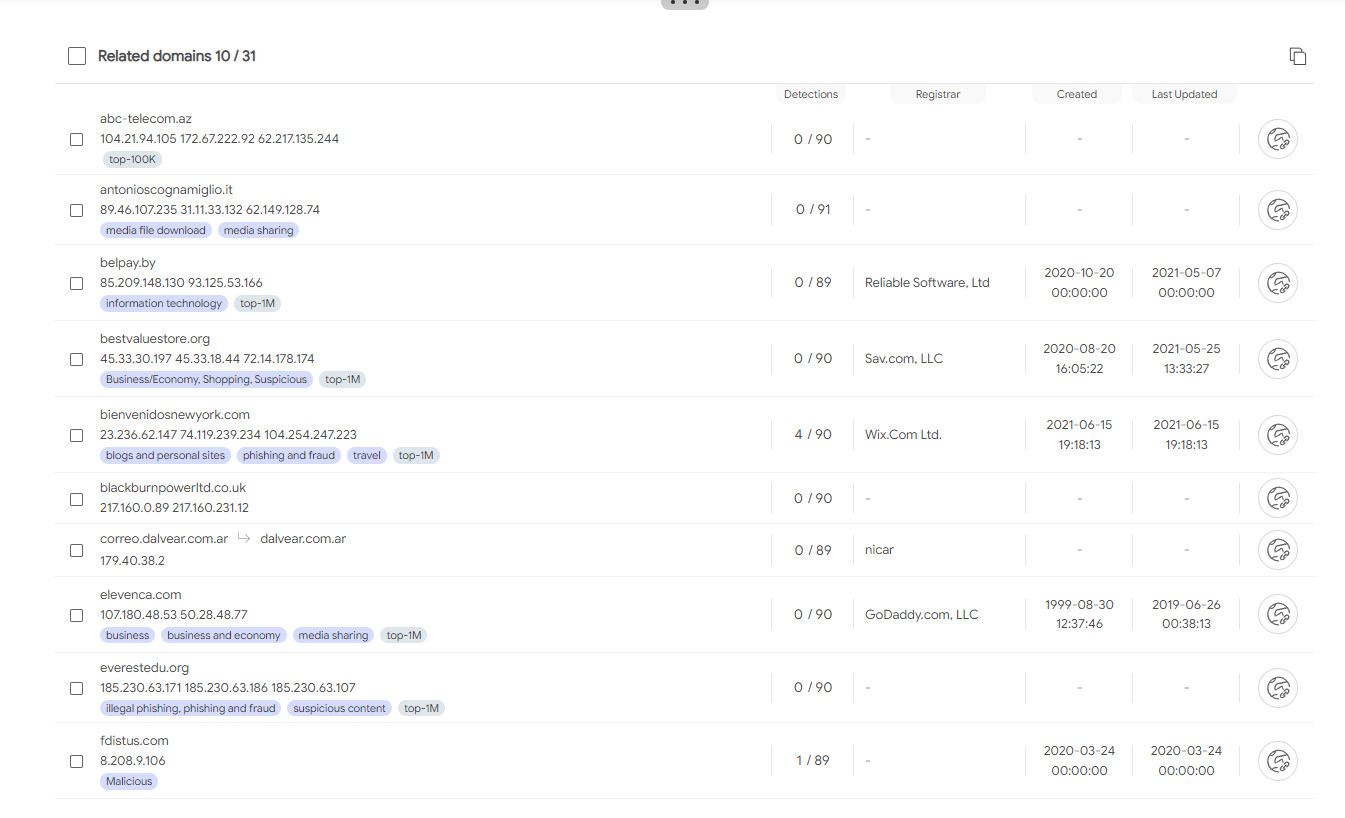
Malpedia’s GandCrab IoC collection of related domains:
Security researchers are applauding the new feature in VirusTotal and have already started to create collections of IoC, which are usually shared via tweets and text storage services.
With Collections, VirusTotal provides a simpler way for threat researchers to collaborate and find actionable intelligence that is easy to access and distribute.