KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







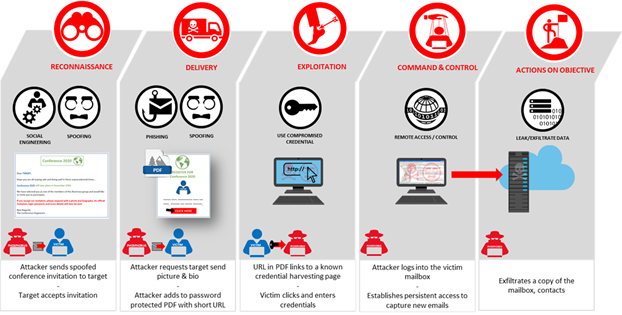
Microsoft disclosed today that Iranian state-sponsored hackers successfully hacked into the email accounts of multiple high-profile individuals and potential attendees at this year’s Munich Security Conference and the Think 20 (T20) summit.
The successful attacks targeted over 100 individuals and were linked by Microsoft’s Threat Intelligence Center (MSTIC) linked to the Iranian-backed hacking group tracked by the company as Phosphorus (known by others as Charming Kitten, APT 35, and Magic Hound).
“The attacks were successful in compromising several victims, including former ambassadors and other senior policy experts who help shape global agendas and foreign policies in their respective countries,” Tom Burt, Corporate Vice President for Customer Security & Trust at Microsoft said earlier today.
Based on MSTIC’s analysis of the attacks, they are part of a cyber-espionage campaign designed to collect intelligence by exfiltrating the victims’ mailbox contents and contact list to the de-ma[.]online, g20saudi.000webhostapp[.]com, and ksat20.000webhostapp[.]com domains used for data harvesting.
Also Read: 5 Common Sections in an Agreement Form Example
To be able to compromise their victims’ email accounts, the Phosphorus actors sent spoofed email invitations “to former government officials, policy experts, academics, and leaders from non-governmental organizations” between February and October 2020.
The attackers were using almost perfect English in the spoofed emails and were masquerading as organizers of the Munich Security or the Think 20 (T20) conferences.
“Based on current analysis, we do not believe this activity is tied to the U.S. elections in any way,” Burt said.
However, last month, Microsoft disclosed another series of attacks where nation state-sponsored hacking groups operating from Russia, China, and Iran were seen targeting organizations and individuals involved in this year’s U.S. presidential election.
As Microsoft said, Phosphorus actors were spotted during May and June 2020 while trying to log into the accounts of both Trump campaign associates and U.S. admin officials, without much success.
“We’ve already worked with conference organizers who have warned and will continue to warn their attendees, and we’re disclosing what we’ve seen so that everyone can remain vigilant to this approach being used in connection with other conferences or events,” Burt added.
Also Read: Limiting Location Data Exposure: 8 Best Practices
Individuals who might have been targeted in these attacks are advised to review any email-forwarding rules to find any out-of-place ones that might’ve been set during a successful hack of their email accounts.
The targeted security conference is known for bringing together hundreds of high-level decision-makers and prominent opinion leaders from all around the world including heads of state, ministers, and NGO leaders.
Think 20 is another policy conference that gathers policy experts and world leaders to draw up policy solutions ahead of each annual G20 summit.