KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft today announced that Microsoft Defender for Endpoint, the enterprise version of its Windows 10 Defender antivirus, now comes with support for blocking cryptojacking malware using Intel’s silicon-based Threat Detection Technology (TDT).
Cryptojacking malware allows threat actors to secretly mine for cryptocurrency on infected devices, including personal computers, enterprise servers, and mobile devices).
In some cases, cryptojacking drastically lowers the infected machines’ performance by hogging valuable system resources.
Intel TDT is part of the Hardware Shield‘s suite of capabilities available on Intel vPro and Intel Core platforms, providing endpoint detection and response (EDR) capabilities for advanced memory scanning, cryptojacking, and ransomware detection via CPU-based heuristics.
Intel TDT couples low-level hardware telemetry collected from the CPU’s performance monitoring unit (PMU) with machine learning to detect cryptomining malware at execution time.
This helps Microsoft Defender block the malicious processes without using hypervisor introspection or code injection to get around detection evasion techniques such as code obfuscation used by malware creators.
Microsoft also wants to use Intel TDT in the future to detect and stop other malware strains and attack techniques such as ransomware and side-channel attacks.
Also Read: The Difference Between GDPR And PDPA Under 10 Key Issues
“Even though we have enabled this technology specifically for cryptocurrency mining, it expands the horizons for detecting more aggressive threats like side-channel attacks and ransomware,” Karthik Selvaraj Principal Research Manager, Microsoft 365 Defender Research Team, said.
“Intel TDT already has the capabilities for such scenarios, and machine learning can be trained to recognize these attack vectors.”
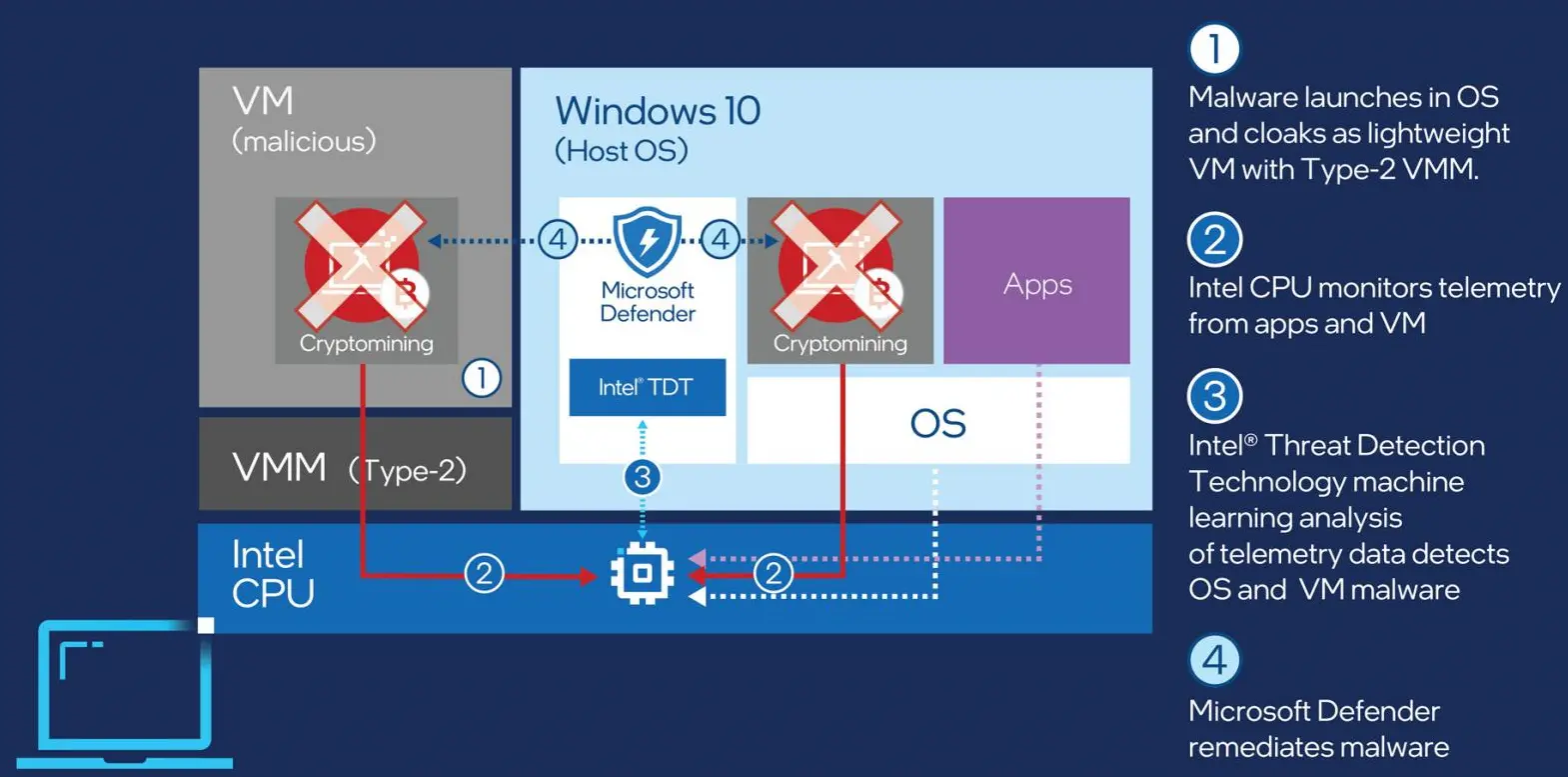
While Intel TDT continuously monitors and analyzes telemetry data from virtual machines and applications for signals of malicious activity, this doesn’t impact the system’s overall performance since it delegates resource-intensive workloads to the integrated graphics processing unit (GPU).
“This advanced threat detection doesn’t create a performance hit requiring IT leaders to make a tradeoff between better security or a good user experience,” Intel added.
“Intel TDT can offload performance-intensive security workloads to the integrated graphics controller and return performance back to the CPU, allowing for increased scanning and reduced impacts to the computing experience.”
The new capability is available for all customers using Intel Core processors and the Intel vPro platform, 6th Generation or later.
“This partnership is one example of our ongoing investment and deep collaboration with technology partners across the industry,” Selvaraj added.
“We work closely with chipmakers to explore and adopt new hardware-based defenses that deliver robust and resilient protection against cyberthreats.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
“As organizations look to simplify their security investments, built-in platform-based security technologies, such as the integration of Intel TDT with Microsoft Defender for Endpoint, combine best of breed in a streamlined solution.”