KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has released emergency out-of-band security updates for all supported Microsoft Exchange versions that fix four zero-day vulnerabilities actively exploited in targeted attacks.
These four zero-day vulnerabilities are chained together to gain access to Microsoft Exchange servers, steal email, and plant further malware for increased access to the network.
For the attack to work, remote attackers would need to access an on-premise Microsoft Exchange server on port 443. If access is available, the threat actors would then utilize the following vulnerabilities to gain remote access:
CVE-2021-26855 is a server-side request forgery (SSRF) vulnerability in Exchange which allowed the attacker to send arbitrary HTTP requests and authenticate as the Exchange server.
CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Exploiting this vulnerability gave HAFNIUM the ability to run code as SYSTEM on the Exchange server. This requires administrator permission or another vulnerability to exploit.
CVE-2021-26858 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
Also Read: How To Comply With PDPA: A Checklist For Businesses
CVE-2021-27065 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
Microsoft has detected a China state-sponsored hacking group known as Hafnium utilizing these attacks against US organizations to steal data.
“Historically, Hafnium primarily targets entities in the United States for the purpose of exfiltrating information from a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks and NGOs.”
“While Hafnium is based in China, it conducts its operations primarily from leased virtual private servers (VPS) in the United States,” Microsoft disclosed in a blog post today.
After gaining access to a vulnerable Microsoft Exchange server, Hafnium would install a web shell that allows them to steal data, upload files, and execute almost any command on the compromised system.
Hafnium would perform a memory dump of the LSASS.exe executable to harvest cached credentials using this web shell.
They would then export mailboxes and stolen data from the Exchange server and upload it to file-sharing services, such as MEGA, where they could later retrieve it.
Finally, Hafnium would create a remote shell back to their servers to access the machine and its internal network.
Due to the severity of the attacks, Microsoft recommends that administrators “install these updates immediately” to protect Exchange servers from these attacks.
Microsoft Senior Threat Intelligence Analyst Kevin Beaumont has created a Nmap script that can be used to scan a network for potentially vulnerable Microsoft Exchange servers.
To use the script, download it from his GitHub page and store it in /usr/share/nmap/scripts and then use the nmap --script http-vuln-exchange command.
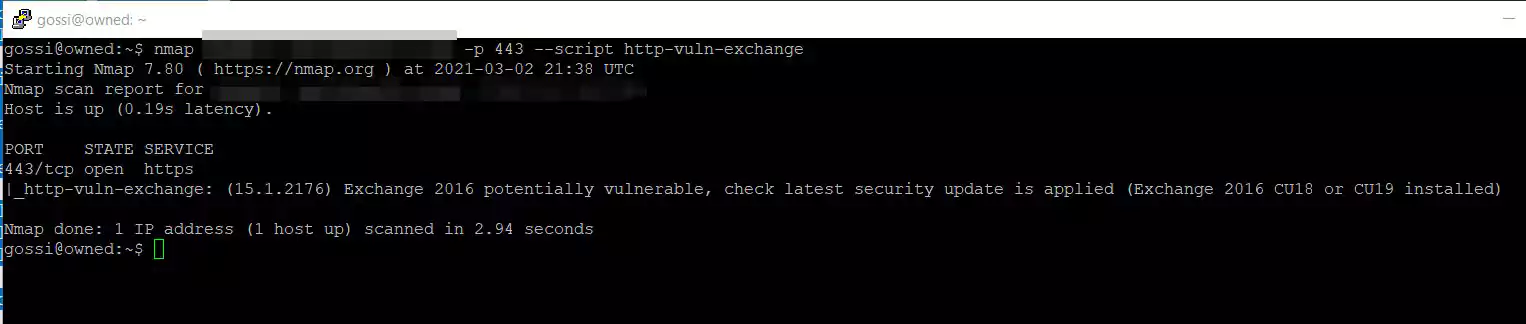
Once you have determined what Exchange servers need to be updated, you need to make sure your servers have a currently supported Cumulative Update (CU) and Update Rollup (RU) installed.
Administrators can find more information on the supported updates and how to install the patches in an article from the Microsoft Exchange Team published today.
Also Read: In Case You Didn’t Know, ISO 27001 Requires Penetration Testing
To detect whether a Microsoft Exchange server has been breached using these vulnerabilities, Microsoft has provided PowerShell and console commands to scan Event Logs/Exchange Server logs for traces of the attack.