KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new ransomware called Pay2Key has been targeting organizations from Israel and Brazil, encrypting their networks within an hour in targeted attacks still under investigation.
Michael Gillespie, the creator of ID Ransomware, has also seen submissions from Pay2Key victims predominantly from Brazilian IP addresses.
Although used in attacks against multiple Brazilian entities, this ransomware is not related to yesterday’s RansomExx attacks targeting Brazil’s government networks.
In a new report by Check Point, researchers say that the threat actors behind Pay2Key ransomware are likely using publicly exposed Remote Desktop Protocol (RDP) to gain access to victims’ networks and deploy the initial malicious payloads.
While the Pay2Key operators infiltrate and are active in the targeted networks before the ransomware begins encrypting systems, they have the “ability to make a rapid move of spreading the ransomware within an hour to the entire network.”
Once inside a victim’s network, the attackers will set up a pivot device that will be used as a proxy for all outgoing communications between the ransomware infected computers and Pay2Key’s command-and-control (C2) servers.
This helps them evade or at least reduce the risk of detection before encrypting all reachable systems on the network by using a single device to communicate with their own infrastructure.
Also Read: Letter of Consent MOM: Getting the Details Right
Just as in the case of other human-operated ransomware operations, Pay2Key actors will use Microsoft’s legitimate PsExec portable tool to remotely execute ransomware payloads named Cobalt.Client.exe on the targeted organizations’ network devices.
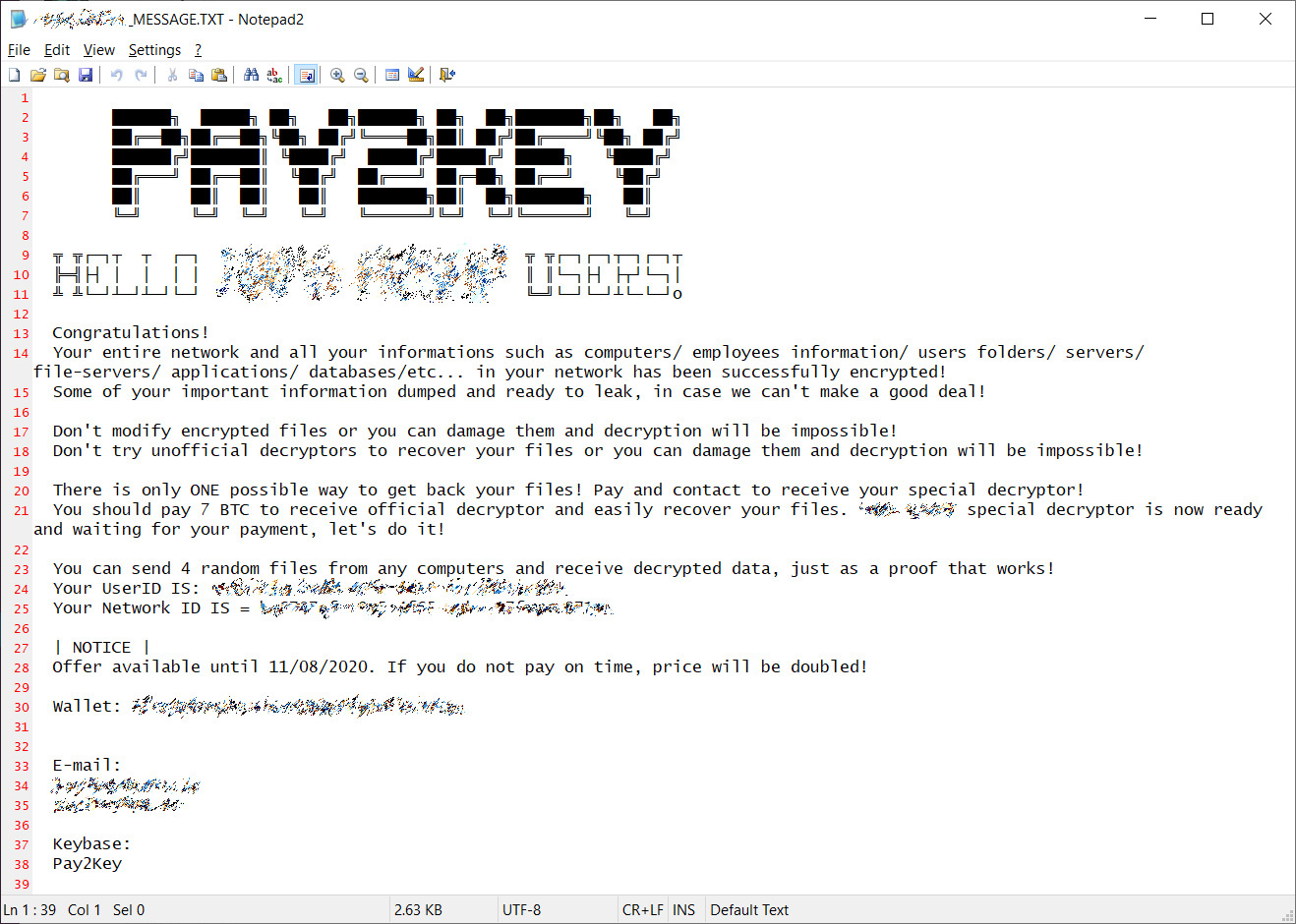
Following successful encryption of a device, the ransomware will drop a ransom note on the system, customized for each compromised organization, and using a [ORGANIZATION]_MESSAGE.TXT name.
The ransom note also mentions that some of the victims’ files was stolen during the attacks but Check Point is yet to find proof of this happening.
Pay2Key operators are currently asking for relatively low ransoms, with Check Point seeing them demand between 7 and 9 bitcoins (roughly $110K-$140K) per victim. BleepingComputer has seen ransom demands as low as 4 bitcoins (around $62K).
This ransomware is not based on code from previously detected strains and Pay2Key samples were only detected by a single antimalware engine when submitted to VirusTotal.
According to compilation artifacts, it also looks like Pay2Key is internally called ‘Cobalt’ by developers who are not native English speakers according to strings and log wording.
The ransomware uses a hybrid of symmetric and asymmetric encryption scheme which employs the AES and RSA algorithms with the C2 server being the one to deliver an RSA public key at runtime which indicates that Pay2Key will fail to encrypt machines without an Internet connection or if the C2 server is offline.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
“While the attack is still under investigation, the recent Pay2Key ransomware attacks indicate a new threat actor is joining the trend of targeted ransomware attacks – presenting well-designed operation to maximize damage and minimize exposure,” the Check Point researchers concluded.