KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Windows Update client has just been added to the list of living-off-the-land binaries (LoLBins) attackers can use to execute malicious code on Windows systems.
LoLBins are Microsoft-signed executables (pre-installed or downloaded) that can be abused by threat actors to evade detection while downloading, installing, or executing malicious code.
They can also be used by attackers in their efforts to bypass Windows User Account Control (UAC) or Windows Defender Application Control (WDAC) and to gain persistence on already compromised systems.
The WSUS / Windows Update client (wuauclt) is a utility located at %windir%\system32\ that provides users partial control over some of the Windows Update Agent’s functionality from the command-line.
It allows checking for new updates and installing them without having to use the Windows user interface but instead triggering them from a Command Prompt window.
Using the /ResetAuthorization option allows initiating a manual update check either on the locally configured WSUS server or via the Windows Update service according to Microsoft.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
However, MDSec researcher David Middlehurst discovered that wuauclt can also be used by attackers to execute malicious code on Windows 10 systems by loading it from an arbitrary specially crafted DLL with the following command-line options:
wuauclt.exe /UpdateDeploymentProvider [path_to_dll] /RunHandlerComServer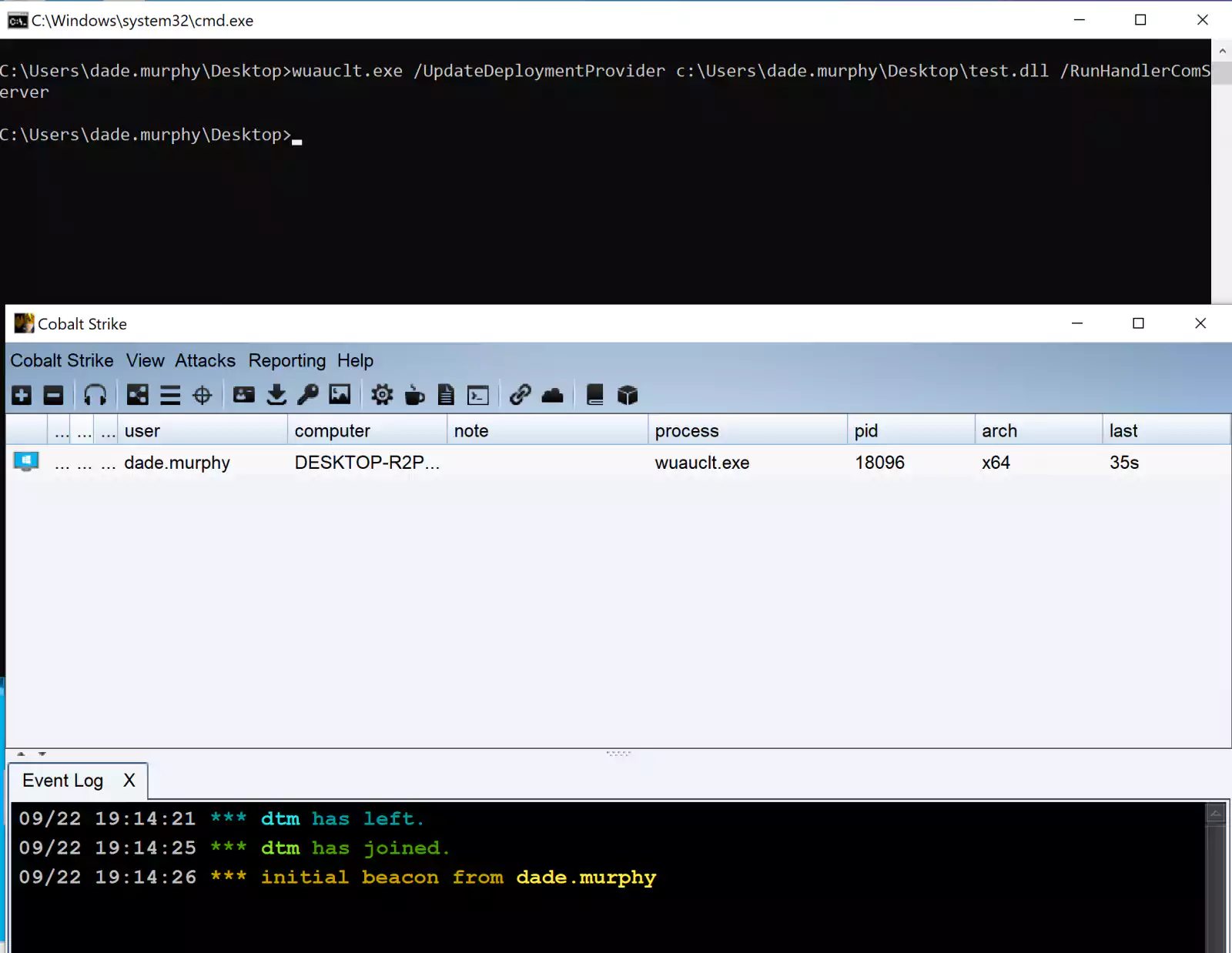
As seen in the screenshot above, the Full_Path_To_DLL is the absolute path to the attacker’s specially crafted DLL file that would execute code on attach.
This defense evasion technique is categorized by MITRE ATT&CK as Signed Binary Proxy Execution via Rundll32 and it enables attackers to bypass anti-virus, application control, and digital certificate validation protection
In this case, it does it by executing malicious code from a DLL loaded using a signed-Microsoft binary, the Windows Update client (wuauclt).
After discovering that wuauclt can also be used as a LoLBin, Middlehurst also found a sample using it in the wild.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
Microsoft recently updated the Windows 10 Microsoft Defender antivirus solution, ironically and quietly adding a way to download files (potentially malicious) onto Windows devices.
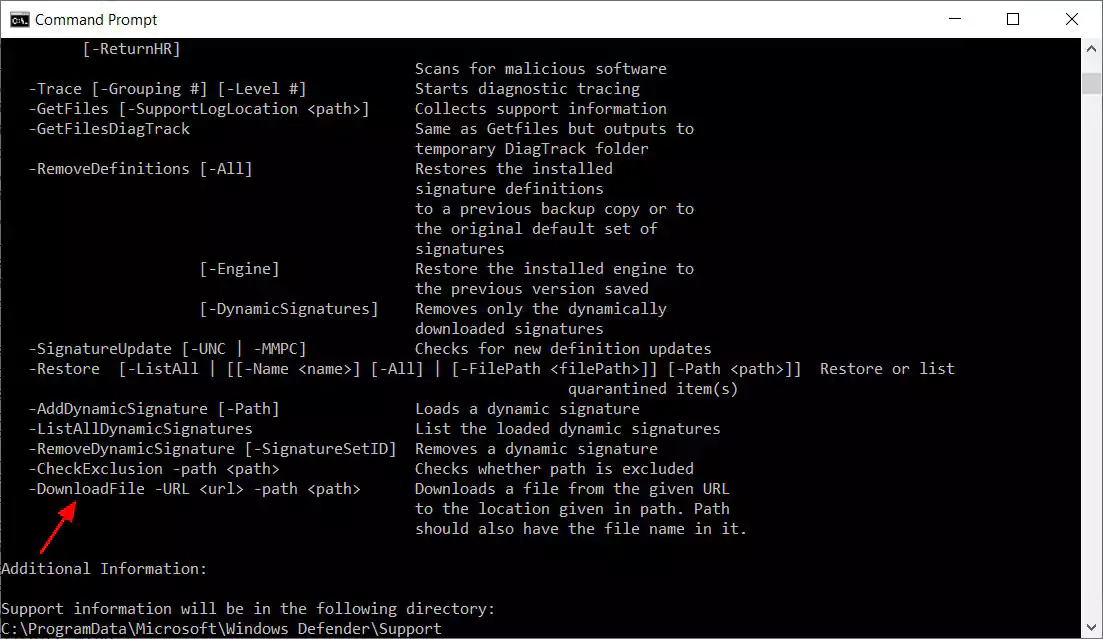
Microsoft later removed the capability from MpCmdRun.exe (the Microsoft Antimalware Service Command Line Utility).
Last month, BleepingComputer also reported that the Microsoft Windows TCPIP Finger command can also be used as a file downloader and as a substitute command and control (C3) server for exfiltrating data.