KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Korean researchers have developed a set of attacks against some solid-state drives (SSDs) that could allow planting malware in a location that’s beyond the reach of the user and security solutions.
The attack models are for drives with flex capacity features and target a hidden area on the device called over-provisioning, which is widely used by SSD makers these days for performance optimization on NAND flash-based storage systems.
Hardware-level attacks offer ultimate persistence and stealth. Sophisticated actors have worked hard to implement such concepts against HDDs in the past, hiding malicious code in unreachable disk sectors.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
Flex capacity is a feature in SSDs from Micron Technology that enables storage devices to automatically adjust the sizes of raw and user-allocated space to achieve better performance by absorbing write workload volumes.
It is a dynamic system that creates and adjusts a buffer of space called over-provisioning, typically taking between 7% and 25% of the total disk capacity.
The over-provisioning area is invisible to the operating system and any applications running on it, including security solutions and anti-virus tools.
As the user launches different applications, the SSD manager adjusts this space automatically against the workloads, depending on how write or read-intensive they are.
One attack modeled by researchers at Korea University in Seoul targets an invalid data area with non-erased information that sits between the usable SSD space and the over-provisioning (OP) area, and whose size depends on the two.
The research paper explains that a hacker can change the size of the OP area by using the firmware manager, thus generating exploitable invalid data space.
Also Read: 5 Common Sections in an Agreement Form Example
The problem here is that many SSD manufacturers choose not to erase the invalid data area to save on resources. This space remains filled with data for extensive periods, under the assumption that breaking the link of the mapping table is enough to prevent unauthorized access.
As such, a threat actor leveraging this weakness could gain access to potentially sensitive information.
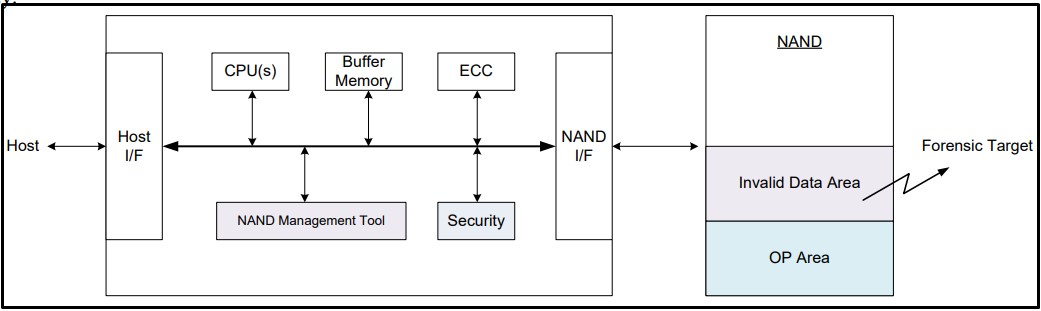
The researchers note that forensic activity on NAND flash memory can reveal data that has not been deleted in over six months.
In a second attack model, the OP area is used as a secret place that users cannot monitor or wipe, where a threat actor could hide malware.
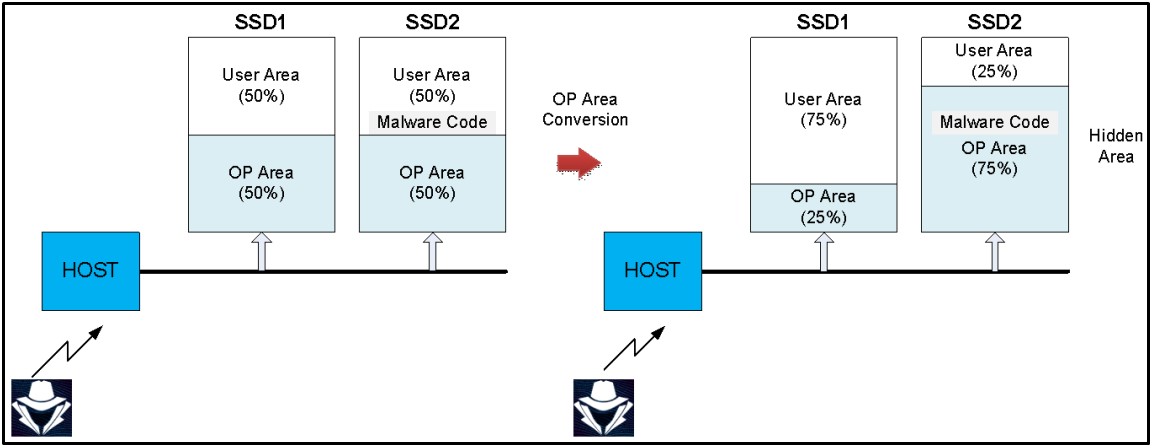
The paper describes this attack as follows:
It is assumed that two storage devices SSD1 and SSD2 are connected to a channel in order to simplify the description. Each storage device has 50% OP area. After the hacker stores the malware code in SSD2, they immediately reduce the OP area of SSD1 to 25% and expand the OP area of SSD2 to 75%.
At this time, the malware code is included in the hidden area of SSD2. A hacker who gains access to the SSD can activate the embedded malware code at any time by resizing the OP area. Since normal users maintain 100% user area on the channel, it will not be easy to detect such malicious behavior of hackers.
The obvious advantage of such an attack is that it is stealthy. Detecting malicious code in OP areas is not only time-consuming but also requires highly-specialized forensic techniques.
As a defense against the first type of attack, the researchers propose SSD makers wipe the OP area with a pseudo-erase algorithm that would not affect real-time performance.
For the second type of attack, a potentially effective security measure against injecting malware in the OP area is to implement valid-invalid data rate monitoring systems that watch the ratio inside SSDs in real-time.
When the invalid data ratio increases significantly all of a sudden, the user could get a warning and the option of a verifiable data-wiping function in the OP space.
Finally, access to the SSD management app should have robust defenses against unauthorized access.
“Even if you are not a malicious hacker, a misguided employee can easily free hidden information and leak it by using the OP area variable firmware/software at any time” – the researchers explain.
Bleeping Computer has reached out to Micron asking for a comment on the above, and we will update this story when we receive a response.
While the research demonstrates that the OP area on Micron SSDs can be used to store malware, it is unlikely that such attacks are taking place in the wild right now.