KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Scammers are targeting your social network accounts with phishing emails that pretend to be copyright violations or promises of a shiny ‘blue checkmark’ next to your name.
With social networks such as Twitter, Facebook, Instagram, and TikTok becoming a significant component in people’s lives, attackers target them for malicious purposes.
These stolen accounts are then used for disinformation campaigns, cryptocurrency scams like the recent Twitter hacks, or sold on underground markets.
Due to this, social accounts should be treated as a valuable commodity and protected as such.
Over the past month, MalwareHunterTeam has been tracking numerous phishing campaigns that target your socials network accounts and has been sharing them with BleepingComputer.
Below we outline the two most common social network phishing scams you may run into so that you know how to avoid them.
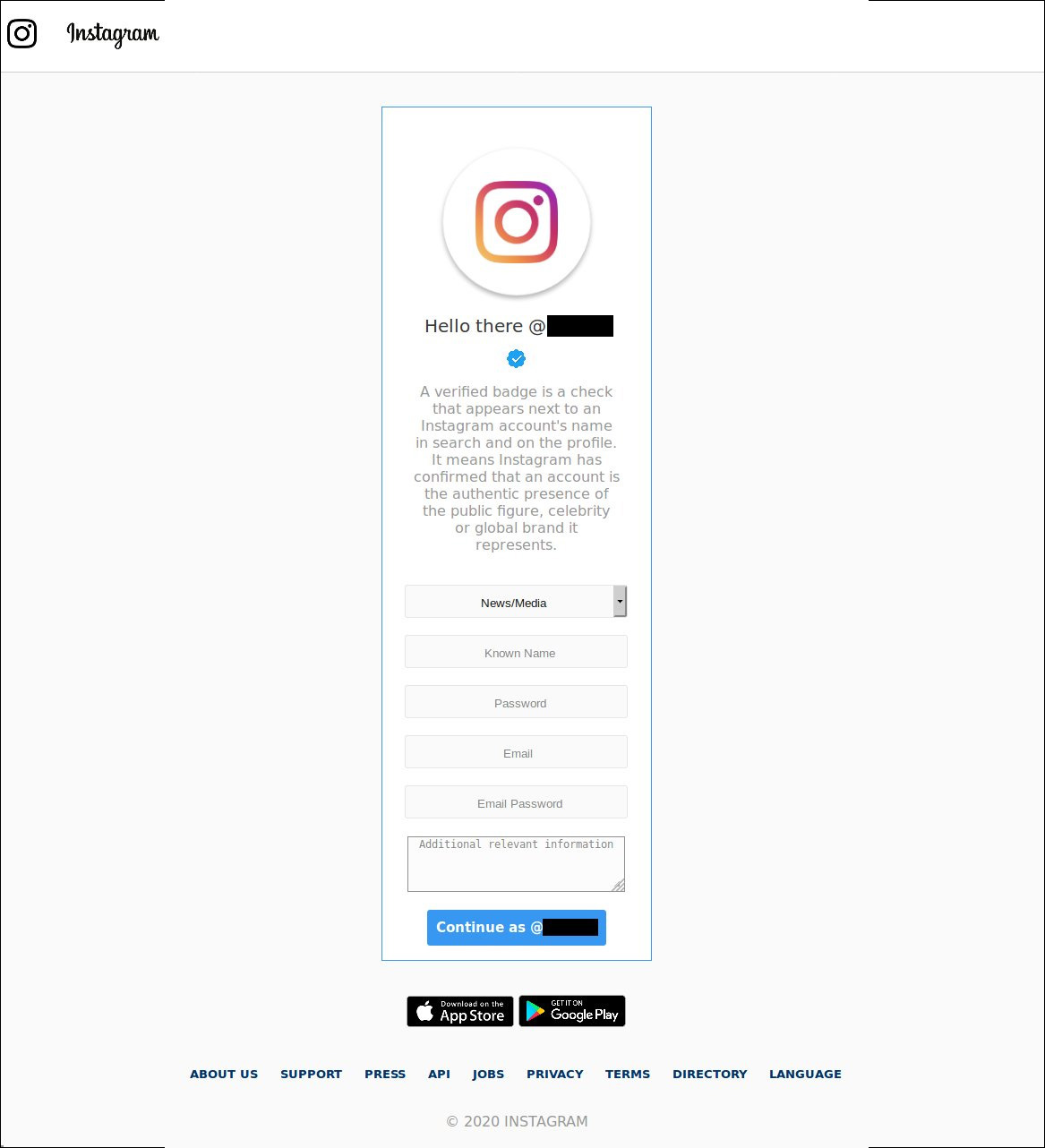
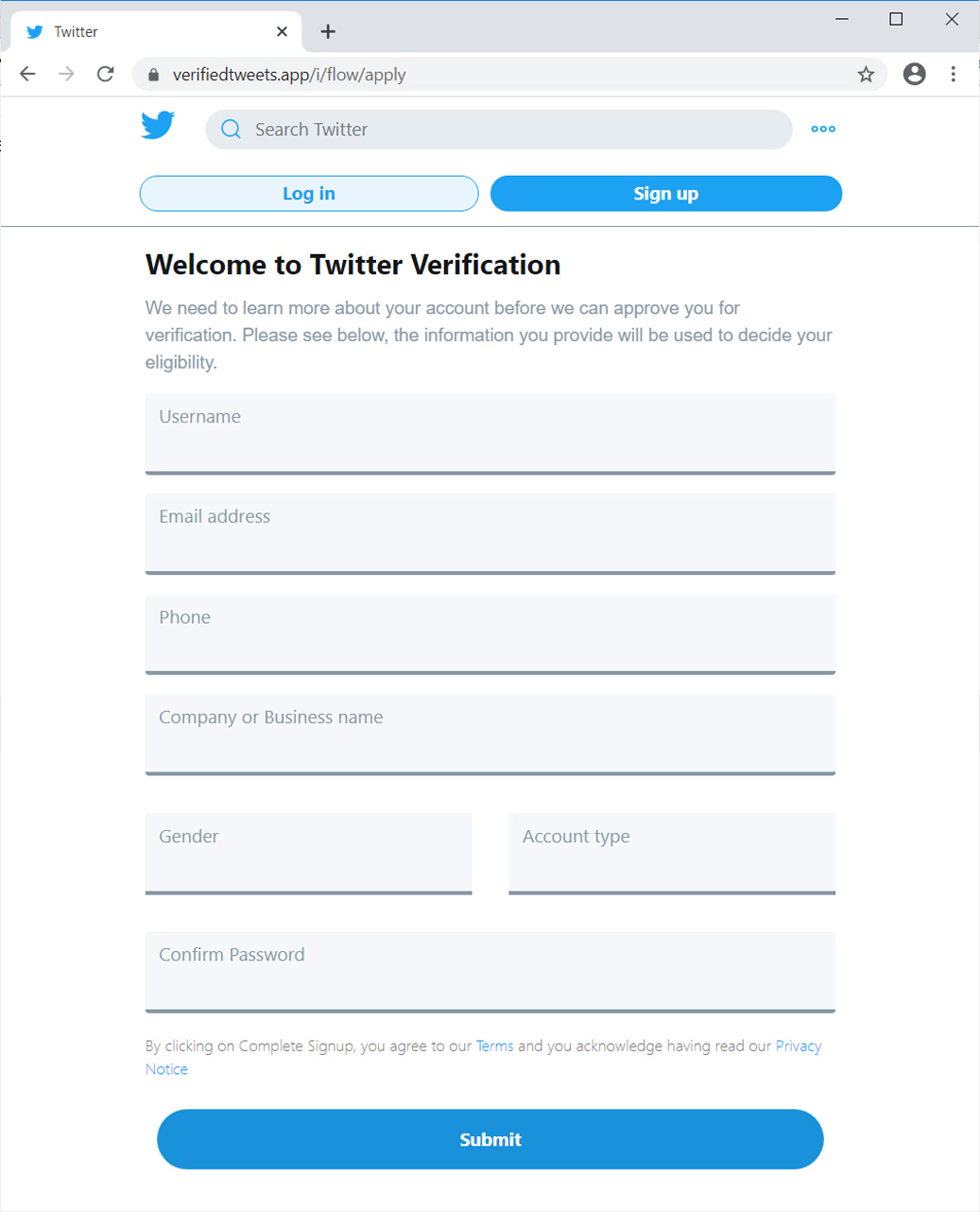
The first phishing campaign has become popular lately as it promises to get you verified checkmark on social networks like TikTok, Instagram, and Twitter.
The most common social networks targeted with this scam are Twitter and Instagram and will prompt users to enter their login and password to get verified.
 |  |
Not as common as Instagram or Twitter, TikTok phishing pages are also being created that promise users a shiny verification badge.
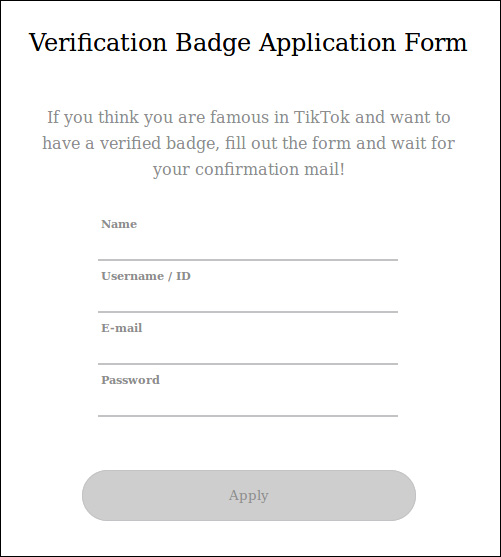
Almost all of the landing pages we have seen pushing these verification scams contain the word ‘verify’ or ‘badge’ in them, so be wary of any URLs containing these strings and claiming to be able to verify your account.
Also Read: By Attending This Event You Agree To Be Photographed
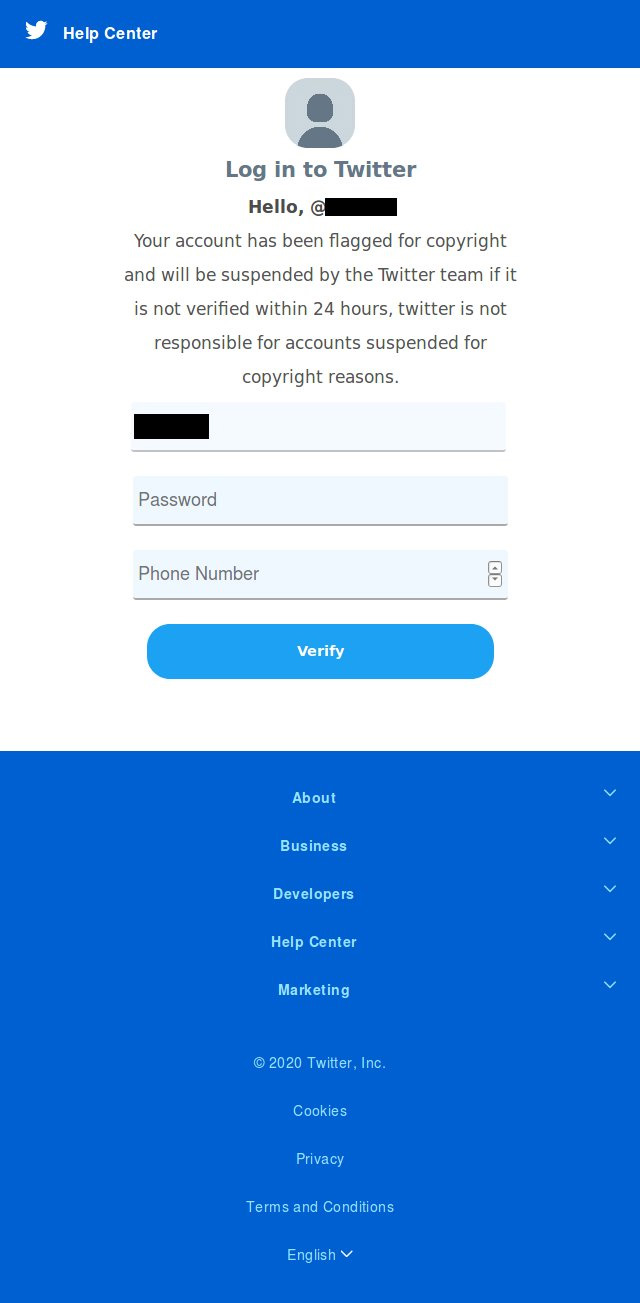
Another widespread social network phishing campaign pretends to be a copyright violation for a post you made.
These phishing pages state that your Twitter or Instagram account will be suspended in 24 hours unless you log in and dispute the copyright infringement claim.
Below you can see an example of recent Twitter and Instagram copyright violation phishing pages.
 | 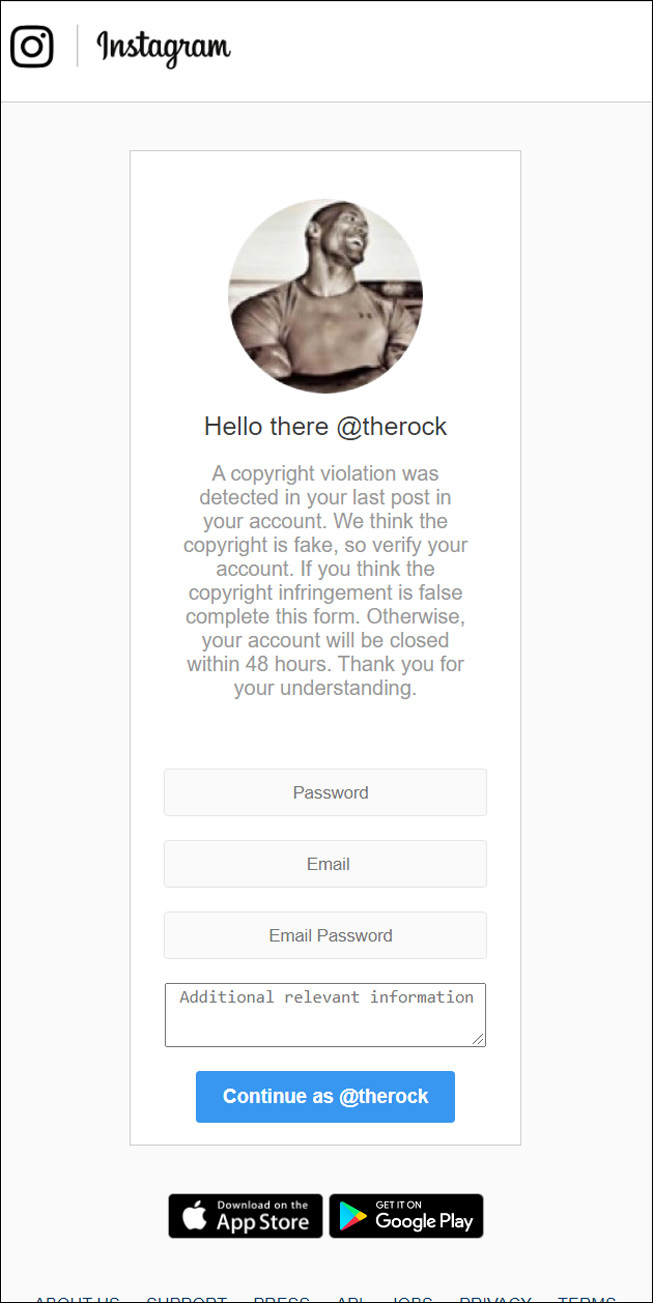 |
What makes the Instagram phishing page interesting is that it will display your actual profile picture on the phishing page to make it appear more legitimate, as shown by the image of Dwayne Johnson above.
It should be noted that the Instagram phishing page above also targets your email account password, as taking over an email account gives a wide range of access to other accounts.
This web sites for these copyright violation phishing pages will usually contain the words ‘copyright’ or ‘violation’ in the URL, which makes them easier to spot.
These scams wouldn’t exist if people didn’t fall for them.
Maybe its lack of sleep, stress at work, or you just got into a fight with your partner; falling for phishing scams can happen by accident.
If you mistakenly fall for one of these scams and enter your login name and password, you should immediately log in to the service and change your password.
You should also enable 2FA/MFA on your social accounts to prevent scammers from stealing your accounts without having access to your mobile phone.
Also, multi-factor authentication should be enabled on your email account, as once attackers gain access, it makes it much easier to steal other accounts you own.
Also Read: 7 Simple Tips On How To Create A Good Business Card Data